Broken Authentication -> Unencrypted Communication
If application allows users to connect to it over unencrypted connections(http). An attacker suitably positioned to view a legitimate user’s network traffic could record and monitor their interactions with the application and obtain any information the user supplies.
Exploitation

In this case,we will try to login as admin with this credential admin:admin, and then sniff the http traffics with wireshark.
Let’s check our wireshark and examine the http traffics
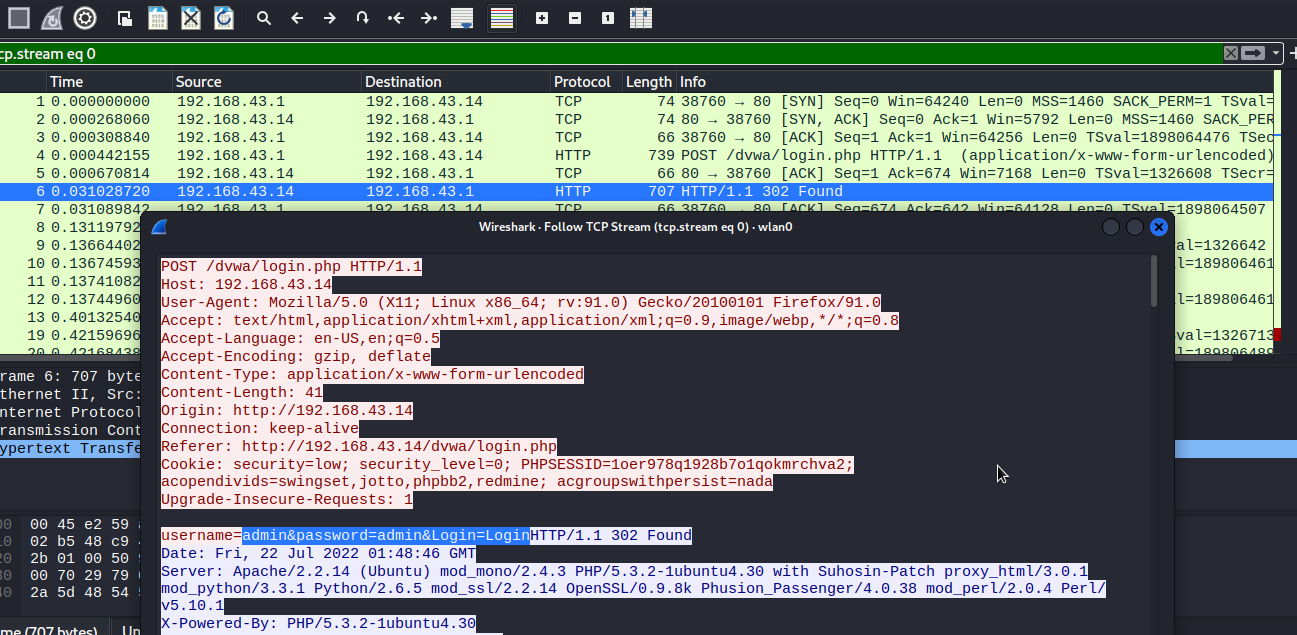
As you can see, we were able to retrieve user’s credentials.
Mitigations
- Use transport-level encryption (SSL/TLS).
- Use Strict-Transport-Security
