Session hijacking : Predictable session token
Session prediction attack focuses on predicting session ID values that permit an attacker to bypass the authentication schema of an application. By analyzing and understanding the session ID generation process, an attacker can predict a valid session ID value and get access to the application.
Exploitation
This webapp uses predictable session token, If we can predict a session token of a user, we will be able to login to his/her account without authentication.
Let’s first login to user account with the following credentials user:user.
We have logged in as user. Let’s analyse the cookies.
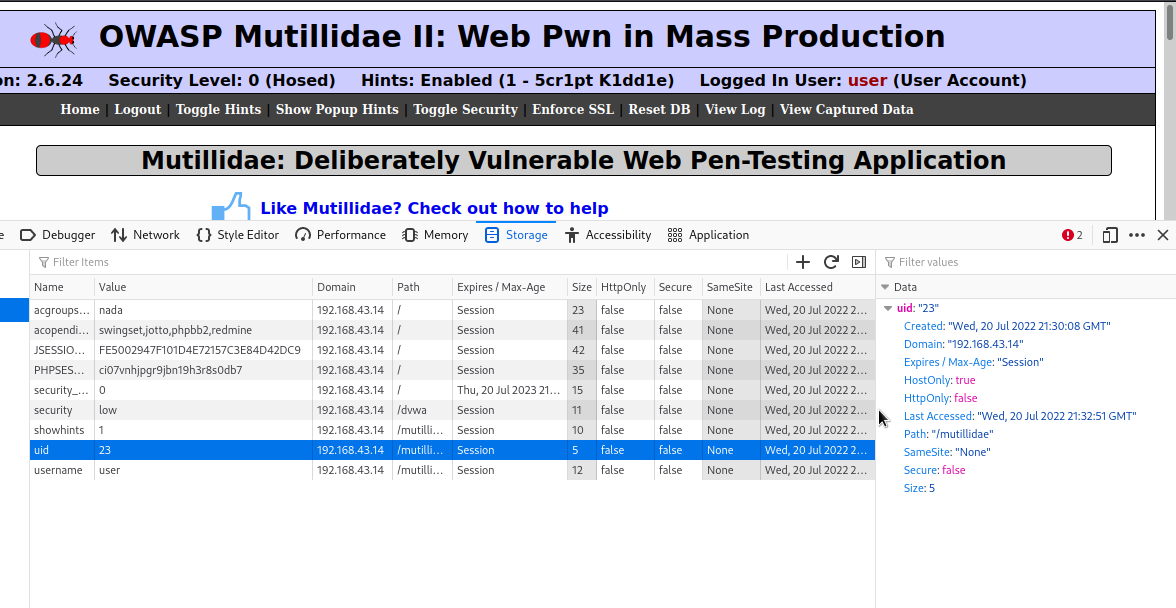
As you can see, session id 23 has been assigned to the user. What if we can change the session id to something else, let’s say 1, we can login to an account of other user. Let’s try
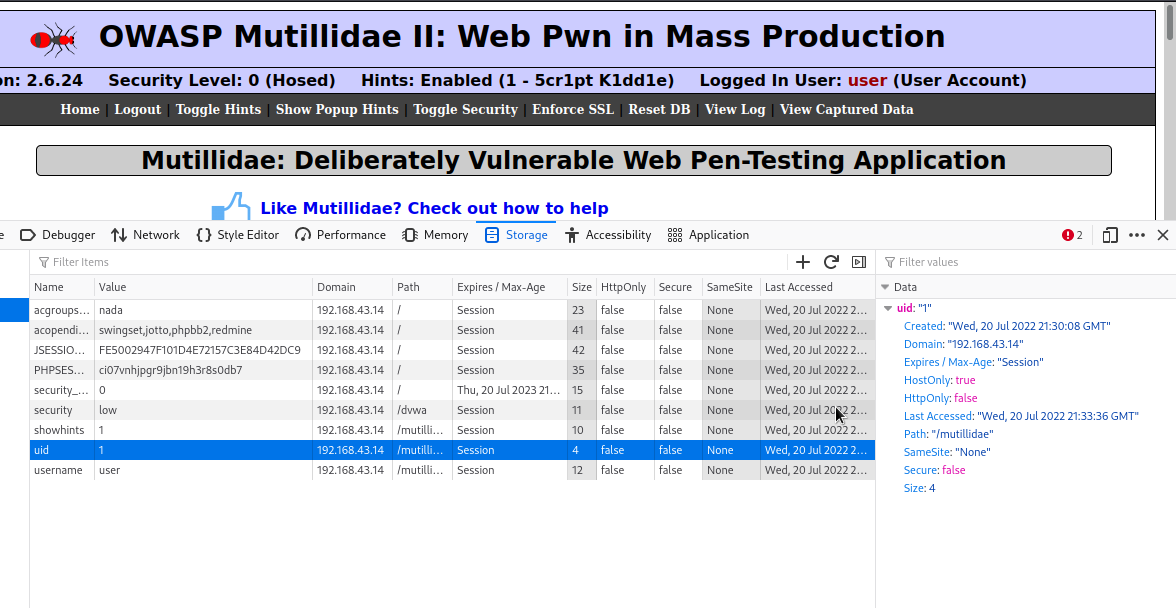
We will refresh the page and see what will happen.
We have logged in as admin.
Mitigations
- Implement unpredictable session id (random enough).
